Welcome back. This is Part 2 of our four-part series on why cyberattacks are successful — and how they actually unfold in real business environments. In Part 1, we examined why cyberattacks succeed even in well-organized companies. The answer isn’t missing technology or neglected security. It’s that risk is systematically misunderstood and underestimated by the very people responsible for managing it.
In this issue, we shift from why to how. Not the final moments when systems lock and data encrypts — but the beginning. The phase where nothing appears broken. Where work continues normally. Where the attack is already underway, but invisible.
Modern cyberattacks don’t announce themselves. They don’t begin with dramatic intrusions or obvious malware. They start quietly, gradually, embedded in the texture of everyday operations. An email that looks legitimate. A login that seems routine. A request that feels reasonable.
By the time an attack becomes visible, the most critical damage has already been done. Understanding this early phase — the phase that feels like nothing — is what this article is about.
The starting point most companies overlook
When people think of cyberattacks, they usually picture the moment something visibly goes wrong: systems suddenly locked, data encrypted, services unavailable, business operations disrupted. This is the phase that feels like the attack — the point at which damage becomes undeniable and response measures begin.
What is often overlooked is that this visible disruption is rarely the beginning. It is the end of a much longer process.
By the time systems are locked or data is encrypted, attackers have already achieved their primary objective: access. They have spent time inside the environment, learned how systems are used, identified valuable data, and understood which activities attract attention — and which do not.
Modern cyberattacks therefore rarely begin with disruption. They begin with access.
And this access is usually gained in ways that look entirely ordinary. A login that succeeds because the credentials are valid. An email that fits seamlessly into existing workflows. A system that has not been updated because it still functions as expected. Nothing appears broken, suspicious, or urgent.
This is the critical starting point most organizations underestimate. Not because it is hidden behind complex exploits, but because it blends into normal business reality.
As long as security is associated primarily with visible incidents, this early phase remains overlooked — even though it is precisely where the outcome of an attack is decided.
This is how modern cyberattacks really begin
Most successful cyberattacks begin in ways that feel entirely familiar to the people involved. There is no dramatic moment, no obvious warning, and no clear signal that something dangerous is happening. Instead, attackers rely on entry points that already exist in everyday business operations.
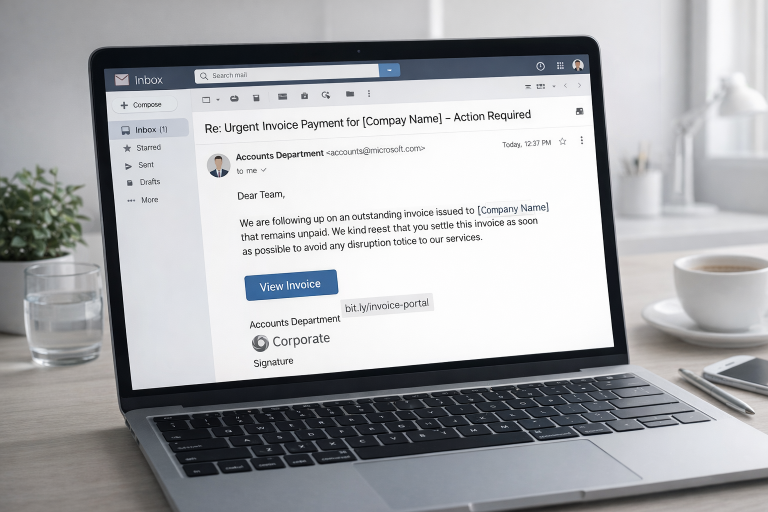
Very often, the first step is an email. Not a poorly written scam message, but a routine-looking request that fits perfectly into ongoing work processes. It references known contacts, current projects, invoices, or shared documents. The language is neutral, professional, and unremarkable. Nothing about it triggers immediate suspicion.
In other cases, the entry point is even quieter. Stolen credentials are used to log into systems exactly as legitimate users would. The login succeeds because the username and password are correct. From the system’s perspective, nothing unusual happens. Access is granted, logs are clean, and alerts remain silent.
Outdated systems play a similar role. Software that still “works” but is no longer maintained offers attackers predictable weaknesses. These systems are rarely attacked aggressively. Instead, they are accessed carefully, often automatically, and then left untouched until the right moment.
Cloud services introduce another layer. They are frequently configured for convenience, speed, and collaboration — not for strict security boundaries. Shared links, broad permissions, and long-lived access tokens make it easy for attackers to move quietly once initial access is achieved.
What all these entry points have in common is that they do not feel like an attack. They feel like normal work.
After initial access is gained, attackers rarely act immediately. They observe. They map the environment, identify valuable systems, and learn which activities attract attention and which go unnoticed. This phase can last days, weeks, or even months.
During this time, business continues as usual. Emails are sent, files are accessed, meetings take place, and systems operate normally. The absence of disruption creates the illusion of safety — even though the attack is already in progress. This is why the beginning of a cyberattack is so difficult to detect. It is designed to blend into routine, not to break it.
Why early attack phases remain invisible
The early stages of a cyberattack are intentionally designed to look normal. Their success depends on the fact that nothing appears unusual, urgent, or out of place. Emails are opened because they match existing workflows and expectations. They refer to familiar topics, ongoing projects, or routine administrative tasks. The language is correct, the timing makes sense, and the request does not stand out from dozens of similar messages received every day.
Logins succeed because credentials are valid. From a technical point of view, the system does exactly what it is supposed to do: it authenticates a known user and grants access. There is no obvious reason to raise an alert, because no rule has been broken.
Files are accessed because permissions allow it. Documents are opened, copied, or modified within the boundaries of existing access rights. Activity stays within normal parameters, and nothing violates predefined security thresholds. From a purely technical perspective, nothing unusual happens.
This is why early attack phases are so difficult to detect. Most security systems are designed to look for anomalies — sudden changes, suspicious patterns, or clearly malicious behavior. Attackers, however, aim for the opposite. They try to behave exactly as expected, blending into normal operations rather than disrupting them.
As a result, organizations often rely on the absence of alerts as a sign of safety. Systems are running, users can work, and no warnings are triggered. Everything appears stable.
In reality, this perceived safety can be misleading. The absence of visible incidents does not necessarily mean the absence of compromise. It often means that the attack is still in its quiet phase — collecting information, expanding access, and preparing the next steps. This creates a dangerous gap between actual compromise and perceived safety. By the time this gap becomes visible, attackers have usually already achieved what they came for.
When detection happens too late
By the time a cyberattack becomes visible, the most decisive phase has already passed. What organizations experience as “the attack” is often only the final manifestation of a process that has been unfolding quietly for a long time.
At this point, access has already been established. Attackers are no longer trying to get in — they are already inside. They have moved laterally across systems, explored internal networks, and identified where valuable data is stored and how it can be accessed without drawing attention.
In many cases, sensitive information has already been copied or prepared for exfiltration long before any disruption occurs. Credentials, customer data, internal documents, or backups may already be in the attacker’s possession. The visible incident does not mark the beginning of damage, but the moment when the damage can no longer be ignored.
The final stage — ransomware deployment, extortion attempts, or service disruption — is often only the last step of a much longer process. It is chosen not because it is technically necessary, but because it creates pressure. Encryption and outages force organizations to react, communicate, and make decisions under stress.
This is why focusing exclusively on “the attack” itself misses the real problem. The decisive phase is everything that happens before: the unnoticed access, the silent observation, and the gradual expansion of control.
When detection happens late, response options become limited. Organizations are forced into reactive mode, dealing with consequences rather than preventing escalation. What feels like a sudden crisis is, in reality, the outcome of a process that remained invisible for too long. Understanding this shift — from visible attack to invisible preparation — is essential. It changes cybersecurity from a question of reaction speed to one of early awareness.
Cybersecurity News – Whats important for 2026
Recent reports from different sectors and countries point to the same underlying reality: cyberattacks are no longer exceptional events. They are part of everyday operations — and they are increasingly shaped by scale, pressure, and silent access rather than spectacular exploits.
In Germany, authorities in Lower Saxony report an average of several serious cyber incidents every single day. Over the past two years alone, thousands of security-related events have been detected and contained. At the same time, the Federal Office for Information Security observes hundreds of thousands of new malware variants emerging daily. This is not a temporary spike, but a sustained shift in the threat landscape — intensified by geopolitical tensions and state-linked activity.
What is striking is not only the volume, but the nature of these incidents. Many attacks do not rely on new vulnerabilities or advanced techniques. They succeed because attackers exploit existing access, overlooked accounts, and normal operational behavior.
A similar pattern is currently affecting the European hotel sector. Instead of attacking central platforms directly, attackers are using compromised email accounts of individual hotels to distribute convincing phishing messages. Customers receive messages that appear legitimate and reference real bookings or systems. According to easybooking, there has been no breach of their core systems — yet the attacks are effective because trust and routine communication are being abused at the edges.
This approach reflects a broader trend: attackers increasingly avoid hardened systems and focus on decentralized, human-facing entry points where detection is harder and responsibility is fragmented.
The pressure created by such incidents becomes visible not only technically, but organizationally. After a major cyberattack that significantly impacted profits, leadership changes followed at Marks & Spencer. While no direct explanations were given, the timing highlights the strain cyber incidents place on organizations and the people responsible for managing them. Cybersecurity is no longer just a technical challenge — it is a leadership and resilience issue.
Taken together, these cases reinforce a central message of this series:
cyberattacks succeed not because defenses are absent, but because access is gained quietly, responsibility is distributed, and early warning signs remain unnoticed.
Understanding how modern cyberattacks really begin is therefore not an academic exercise. It is essential for navigating a threat landscape where silence, routine, and normal operations are increasingly used as attack vectors.
Security misconception of the week
“We would notice immediately if something was wrong.”
This assumption feels reassuring — and in everyday business life, it seems logical. If systems are running, emails are being sent, and work continues as usual, it is easy to conclude that everything is fine. In reality, this belief is one of the most dangerous misconceptions in cybersecurity.
Early attack phases are not designed to trigger alarms or draw attention. They are designed to remain invisible. Attackers deliberately avoid actions that would look suspicious, disruptive, or out of place. Their goal is not to be fast, but to be unnoticed.
Many companies only realize something is wrong when attackers decide to reveal themselves — through encryption, extortion, or disruption. By then, the critical phase has already passed, and response options are limited.
Understanding that attacks are meant to stay invisible for as long as possible is a crucial step toward realistic cybersecurity. Detection is not about waiting for obvious signs of failure. It is about questioning assumptions and understanding that “nothing unusual” does not always mean “nothing is wrong.”
Insight of end January – The invisible phase
The most underestimated phase of a cyberattack is not the moment of impact. It is the beginning. This early phase is invisible by design. Access looks legitimate, activity appears normal, and systems behave exactly as expected. From the outside, there is no clear signal that something is wrong — and this is precisely why this phase is so effective.
When organizations base their security decisions primarily on alerts, disruptions, or visible incidents, they are already one step behind. By the time alarms are triggered or services are affected, attackers have often completed the most important part of their work. They have observed workflows, expanded access, and identified valuable data — all without raising suspicion.
The key insight is this: Speed of reaction matters far less than early visibility.
Organizations that focus only on reacting quickly once an incident occurs often overlook the silent period in which the outcome of an attack is actually decided. Effective cybersecurity therefore shifts attention away from dramatic events and toward subtle signals: unexpected access patterns, slowly expanding permissions, or behavior that is technically valid but contextually unusual.
Recognizing the invisible phase requires a change in perspective. It means questioning assumptions, understanding normal behavior deeply, and accepting that “nothing unusual” does not automatically mean “nothing is wrong.” This insight is critical, because the earlier a compromise is recognized, the more options remain. Early visibility does not prevent every attack — but it determines whether an incident remains manageable or turns into a crisis.
Tips for your company – increasing visibility early
When it comes to the early phases of cyberattacks, prevention is rarely about adding more tools. It is about improving visibility and awareness in areas that are often taken for granted.
Here are a few practical steps companies can take to better recognize early attack signals — without major investments or complex changes:
Review what “normal” actually looks like
Early attacks hide in routine. Make sure there is a shared understanding of what normal access, normal logins, and normal data usage look like in your organization. Without this baseline, unusual behavior cannot be recognized — even if it is visible.
Pay attention to access, not just alerts
Instead of focusing solely on security alerts, regularly review who has access to which systems, accounts, and data. Over time, permissions tend to grow quietly. Attackers benefit from excessive access far more than from technical vulnerabilities.
Treat silence with caution
No alerts does not automatically mean no risk. Ask critical questions when nothing changes for a long time: Are logs reviewed? Are account activities checked occasionally? Are inactive or rarely used accounts still necessary?
Strengthen awareness around routine actions
Many early attack steps rely on routine behavior: opening emails, approving access, sharing files. Encourage teams to question requests that technically look correct but feel slightly out of context — especially when timing or urgency seems unusual.
Regularly revisit assumptions
Security decisions made years ago may no longer reflect how your organization works today. Cloud usage, remote access, and collaboration tools evolve quickly. Periodic reviews help close gaps created by change, not by neglect.
These steps do not stop every attack. But they significantly reduce the likelihood that early attack phases remain unnoticed — and that is often what makes the difference.
Conclusion: How modern cyberattacks really begin
Understanding how modern cyberattacks really begin fundamentally changes how cybersecurity should be approached. Attacks do not start with disruption, alerts, or visible damage. They start quietly, embedded in normal business processes, trusted workflows, and legitimate access. The earliest stages are successful precisely because they do not look like attacks at all. They look like routine.
This is why many organizations focus on the wrong moment. By the time an incident becomes visible, attackers have often already achieved their goals. Access has been established, systems have been explored, and sensitive data may already be prepared for misuse or exfiltration.
Recognizing how modern cyberattacks really begin shifts the focus from reacting to crises toward identifying risk much earlier. It highlights the importance of visibility, realistic assumptions, and an understanding of how attackers think and operate long before any alarm is triggered.
Cybersecurity does not fail because companies are careless. It fails when the early phases of an attack remain misunderstood. This insight is critical — because what happens before an attack becomes visible ultimately determines how severe the consequences will be.
What’s next
This was Part 2 of a four-part series on why cyberattacks are successful — and how they unfold in real business environments.
In this issue, we looked behind the scenes at how modern cyberattacks really begin: quietly, gradually, and often hidden in normal workflows and legitimate access. Understanding this early phase is essential, because it is where the outcome of an attack is usually decided.
In the next issue, we will take the next step and focus on where organizations unknowingly expose themselves. We will look at how small, everyday decisions — made for convenience, speed, or efficiency — can quietly increase risk over time, without anyone consciously choosing to lower security.
This part of the series will connect the invisible beginnings of attacks with the structures, routines, and assumptions that allow them to succeed. Because security does not start with software. It starts with understanding.
Cybersecurity Insights for Decision-Makers
Not another newsletter.
This is a curated security briefing for business owners and decision-makers who want clarity — not noise.
You’ll receive:
concise explanations of how real attacks start and spread
early-stage warning patterns most companies overlook
practical security decisions you can actually act on
No spam. No marketing sequences. Just insights that help you think clearly about risk before it becomes expensive.
I recommend to reading the follow articels:
5 Red Flags That Your Business May Already Be in a Hacker’s Crosshairs
Cybersecurity 2026: The Biggest Risks for Businesses – and How to Protect Your Company
I’m Too Small to Be a Hacker” – The Most Expensive Mistake in the Middle Class
Why cyberattacks are successful: Understanding the real causes (Part 1 of 4)