
All computers locked – what to do in the event of a ransomware attack?
Imagine this: It’s an ordinary Monday morning. The coffee machine…



Imagine this: It’s an ordinary Monday morning. The coffee machine…

What happens in the first hours after a cyberattack? Let’s…

Welcome back. This is Part 2 of our four-part series…
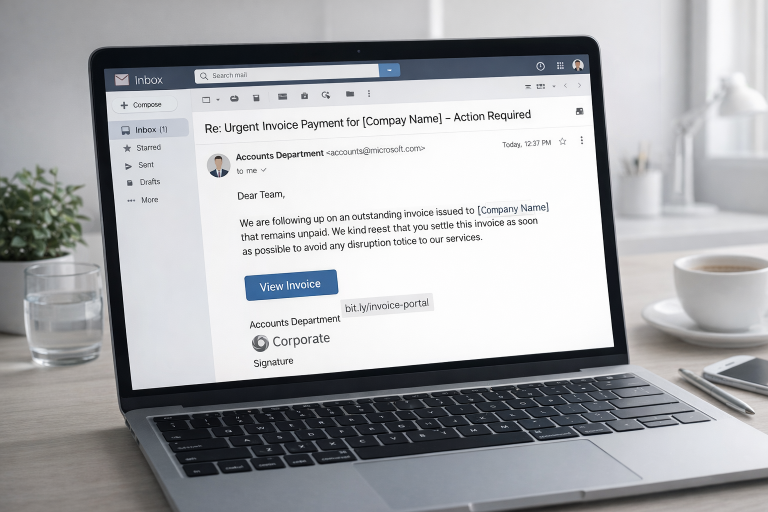
Phishing has changed a lot in recent years. What used…

Cybersecurity is no longer a purely technical issue. It has…

Why shutting down systems during ransomware is dangerous, find it…

Artificial intelligence has become the most dangerous double-edged sword of…

In 2026, relying on a single weak password – or…

Cybersecurity is now a core requirement for businesses. Digital threats…