For most small and medium-sized businesses, the real danger begins with something completely ordinary: the browser your team uses every day. It has quietly become the central entry point to your digital operations. Employees use it to log into cloud tools, handle finances, access customer information, communicate, download files and manage almost every part of the business.
This makes the browser far more than a simple tool. It is the gateway to your entire digital identity — and attackers know it. That’s why cybercriminals increasingly exploit the browser itself instead of breaking into well-protected servers. One fake update message, one compromised website or one malicious extension can be enough to give an attacker silent access to your systems.
A browser attack doesn’t look like a classic hack. There’s no pop-up, no warning, no locked screen. Everything appears normal while an intruder quietly collects data in the background.
Understanding these hidden risks has become essential for modern businesses. The good news: with a few targeted changes, you can dramatically reduce your exposure — without needing a full IT department.
1. The Browser Is the Primary Gateway to All Your Accounts
Most business owners underestimate just how central the browser has become to their daily operations. Years ago, companies relied on local software, internal servers, and isolated tools. Today, almost everything runs in the cloud — and every cloud service is accessed through the browser. That makes it the single most critical point of entry into your digital infrastructure.
Think about a normal workday: Your team starts the morning by opening their browser. Within minutes, they are logging into email accounts, checking customer conversations, opening project management boards, approving invoices, accessing banking portals, updating CRM entries, and browsing through cloud documents. All of these actions depend on the browser functioning as a “trusted interface.” Your employees assume that anything they see in the browser is legitimate, safe, and controlled. Unfortunately, this trust creates exactly the opportunity attackers are waiting for.
If a hacker gains access to the browser, they don’t just compromise a single device — they compromise every account and every system connected to it. Suddenly, sensitive information like quotes, contracts, financial data, tax documents, client messages, support tickets, and internal operations become visible. And because most accounts remain logged in all day, an attacker does not even need your password. They simply ride along on your active session and observe (or manipulate) everything in real time.
This is what makes the browser fundamentally different from other attack surfaces: It is deeply integrated into your work and constantly connected to valuable information. A compromised browser is essentially a compromised business — without the attacker ever having to break into a server, bypass a firewall, or exploit a traditional vulnerability. One weak link in the browser environment is enough to open the entire digital ecosystem behind it.
Many breaches start with something as simple as a malicious website, a fake login window, a compromised extension, or a hidden script on a page. Yet the consequences can be severe: stolen client data, unauthorized payments, hijacked email accounts, or full access to your online platforms. The browser acts like the “master key” to your digital operations — and that is exactly why it deserves far more protection and attention than most companies currently give it.
2. Session Hijacking: The “Silent Breach” Most Companies Never Notice
Session hijacking is one of the most dangerous and least understood browser-based threats. Most business owners have never heard the term, yet almost every company is vulnerable to it because modern browsers prioritize convenience over security. To keep work flowing smoothly, browsers store session cookies that keep you logged into email accounts, CRM systems, accounting tools and cloud platforms without the need to re-enter passwords. This seems practical, but it creates an invisible weak point.
If an attacker manages to steal these session cookies — even once — they can slip directly into your accounts without requiring a password or two-factor authentication. They simply load the stolen session on their own system, and the cloud service treats them as if they were you. No warnings, no login alerts, no unusual activity messages. Everything appears legitimate because the session itself is legitimate. This is what makes session hijacking so dangerous: it effortlessly bypasses every layer of security you believe is protecting you.
Once inside, an attacker can quietly read emails, download customer information, alter invoices, browse shared drives, impersonate you inside collaboration tools, reset passwords or even install hidden integrations that provide ongoing access. And because all of this happens within your active session, nothing looks suspicious. The browser behaves normally while someone else observes or manipulates your data in the background.
These attacks are especially common in small and medium-sized businesses where employees often work from cafés, coworking spaces, home networks or unsecured Wi-Fi. A single compromised website can expose a session cookie through hidden scripts. A seemingly harmless browser extension can capture active sessions. Even a man-in-the-middle attack on a public network can intercept them without leaving behind any visible trace.
What makes session hijacking even more unsettling is that most companies never realize it happened. They only notice unusual transactions, missing files, account changes or unexpected logins long after the attacker has left. By then, the breach appears to have no identifiable origin because the initial compromise left no clear evidence.
For cybercriminals, it is the perfect crime — fast, silent, efficient and incredibly profitable. And for businesses, it is a powerful reminder that security must go far beyond strong passwords and two-factor authentication. Hardening the browser, securing networks, limiting extensions and monitoring sessions are essential steps to ensure that a quiet attack does not succeed long before anyone notices something is wrong.
3. Malicious Extensions Are the New Trojan Horse
Browser extensions were created to make digital work smoother and more efficient. Tools like password managers, grammar checkers, ad blockers, screenshot helpers, AI assistants and cloud storage integrations sit quietly in the background and blend naturally into an employee’s workflow. Because they are used every day, they quickly become trusted tools — almost invisible and rarely questioned. Yet behind this convenience lies one of the fastest-growing attack vectors in modern cybersecurity: malicious or compromised extensions.
Many business owners underestimate how much access a single extension receives the moment it is installed. An extension can read everything displayed inside the browser, from emails and CRM data to invoices, internal dashboards, cloud documents and private messages. It can monitor visited websites, record keystrokes, capture cookies, alter webpage content or inject its own scripts — all without ever revealing its true purpose. This level of access effectively gives an attacker full visibility into the user’s digital activity.
What makes this threat even more alarming is that even legitimate extensions can turn malicious over time. Cybercriminals increasingly buy abandoned or low-maintenance extensions from overwhelmed developers. After the purchase, they push silent updates loaded with tracking scripts, advertising injectors or fully fledged malware. Because these updates come through official browser stores, they are automatically installed without raising suspicion. A tool that once improved productivity transforms into a surveillance weapon almost overnight.
Extensions make ideal Trojan horses because they bypass traditional security tools. Antivirus programs typically scan downloaded files, but extensions live entirely inside the browser environment, where they operate without triggering standard detection systems. Employees rarely notice anything unusual. The extension continues to function normally while quietly siphoning data, redirecting users to impostor login pages or harvesting session information that allows attackers to slip into business accounts unseen.
This risk is amplified in small and medium-sized businesses, where employees often have the freedom to install whatever tools they find useful. Many assume that anything available in the Chrome Web Store or Microsoft Edge Add-ons Store must be safe, but unfortunately, this trust is misplaced. Several major breaches in recent years were traced back to extensions that appeared harmless — sometimes even popular — but had been compromised long after their initial release.
In many cases, companies never realize that an extension was the root cause of the breach. The attacker’s activity blends perfectly into everyday workflow, leaving no obvious signs of wrongdoing. By the time unusual transactions, redirected banking pages or unauthorized account access are noticed, the malicious extension has already done its damage.
The safest approach for businesses is to limit browser extensions to a minimal, approved list and remove everything that is not essential. Allowing employees to install random tools “because they are helpful” introduces far too much risk. In today’s threat landscape, the boundary between a useful extension and a harmful one is thinner than ever, and one careless installation can escalate into a full-scale business breach.
4. Fake Browser Updates — A Growing Threat in 2026
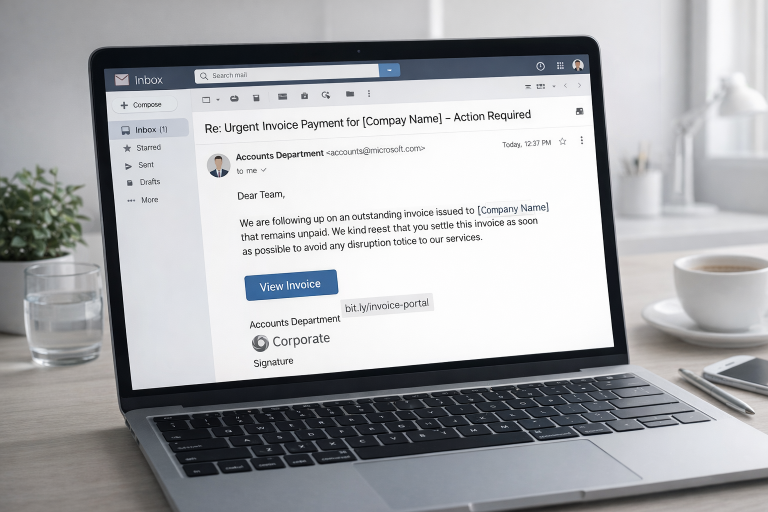
One of the simplest yet most effective ways attackers break into a business system is by exploiting something employees are trained to do without hesitation: installing browser updates. Modern browsers like Chrome, Edge, Firefox and Brave release updates frequently to fix vulnerabilities, so people have become accustomed to clicking “Update now” the moment a prompt appears. Cybercriminals take advantage of this habit.
Over the past two years, fake browser update attacks have surged dramatically. Hackers create websites — some built for malicious purposes, others legitimate sites that have been compromised — that display convincing pop-up messages informing users that their browser is outdated. These messages perfectly imitate the design and wording of genuine Chrome or Edge alerts, leaving no obvious signs that anything is suspicious. What looks like a routine update is actually the entry point to a silent breach.
The moment an employee clicks the fake update button, the system downloads malware disguised as a browser patch. From that point on, the attacker gains an invisible foothold on the device and often inside the browser itself. The malware is engineered to operate quietly. It does not announce its presence or alter the browser’s appearance. Instead, it collects information in the background, harvesting passwords, stealing session cookies, taking screenshots, monitoring keystrokes, manipulating search results or even redirecting online banking pages. Some variants install additional modules over time or create hidden backdoors that allow attackers to re-enter whenever they choose.
The danger lies not only in the technical sophistication but also in the psychological manipulation. Employees trust update prompts because they associate updating with improved security. When someone believes they are making the browser safer, they let down their guard — and that makes them far more likely to install something harmful. This combination of familiarity and trust is what makes fake update attacks so effective.
In 2025, these campaigns have become highly targeted. Hackers tailor their fake prompts to the victim’s browser type, operating system and even language settings. Some attacks only trigger when the user visits certain industry-related sites or when their IP address suggests a valuable business. The goal is to make the fake prompt look as natural and credible as possible, increasing the chances that someone clicks without hesitation.
Small and medium-sized businesses are particularly vulnerable because many rely on manual updates rather than centralized patch management systems. Employees browsing supplier portals, industry forums or online tools are far more likely to encounter a fake update page — and far less equipped to recognize the danger.
Defending against this type of attack requires a simple but powerful shift in mindset: browser updates should never be installed from pop-ups or website messages. Instead, employees should be trained to update only through the browser’s internal settings menu. This one habit dramatically reduces the risk of infection and protects the business from a silent takeover that begins with an innocent click on a message that appeared helpful.
5. Drive-By Malware: Infection Without Clicking Anything
Drive-by malware represents one of the most unsettling developments in modern cybercrime because it removes the one element most businesses rely on for safety: user awareness. Traditionally, people believed malware required a deliberate action — downloading a file, opening an attachment or installing an untrusted program. Today, that assumption is dangerously outdated. Simply visiting the wrong website can be enough to compromise an entire business system.
A drive-by attack exploits vulnerabilities in the browser itself, in a browser extension or in scripts running on the page. The moment an employee loads the site, malicious code can execute silently in the background. There are no pop-ups, no alerts and no indication that anything is wrong. The user continues browsing normally, unaware that invisible processes have already begun to infect the system.
What makes these attacks so deceptive is that they often originate from websites that appear completely legitimate. An industry blog, a supplier portal, a tool your team uses daily, a news site or even a fully trusted page can become dangerous if third-party ad networks or embedded scripts are compromised. Attackers frequently target advertising networks because a single malicious ad banner allows them to distribute malware across thousands of reputable websites at once. A business doesn’t need to visit a suspicious link — a single compromised ad on a trusted page is enough.
Once activated, drive-by malware can serve multiple purposes depending on the attacker’s objective. Some variants quietly steal session cookies or autofill data. Others redirect users to fake login pages designed to harvest credentials. More advanced strains install modules for keylogging, screenshot capture or credential theft. In extreme cases, the browser itself becomes hijacked, routing all traffic through malicious servers that monitor or manipulate every action the user takes.
A growing trend is cryptojacking, where attackers use the victim’s device to mine cryptocurrency. This type of malware stays silent while consuming system resources. Employees may notice that their computer feels unusually warm, the battery drains quickly or the fans run constantly, but they rarely suspect a browser-based infection. Meanwhile, attackers profit by exploiting the company’s hardware.
Drive-by malware is especially dangerous for businesses because it spreads quickly and without detection. A single infected employee can expose shared drives, cloud storage and internal communication platforms. Remote workers using unsecured home networks or public Wi-Fi face even higher risks, turning what should be simple browsing into a possible entry point for a much larger breach.
The psychological challenge is just as significant as the technical one. Since employees do not “do anything wrong,” companies often struggle to understand how the infection began. There are no suspicious downloads, no attachments to analyze, no obvious clues. By the time unusual behaviour such as redirects, browser instability or unexpected account notifications appears, the attacker may have already extracted sensitive data or installed persistent access points.
The most effective defence against drive-by attacks is not traditional antivirus software but restricting what the browser is allowed to execute. Script blockers and advanced ad blockers significantly reduce opportunities for malicious code to run in the background. When combined with regular patching, a controlled extension environment and improved network security, businesses can eliminate a large portion of the risk.
Drive-by malware makes one thing clear: in today’s threat landscape, you don’t have to make a mistake to get hacked. Simply opening a webpage can be enough — and that makes browser security one of the most critical foundations of modern business protection.
6. Autofill: A Helpful Feature That Gives Too Much Away
Autofill is one of the most convenient features built into modern browsers. It saves time, reduces repetitive typing and allows employees to work faster by automatically completing names, email addresses, company details, billing information and even login fields. Because it feels harmless and improves efficiency, most people never question how it actually works. Yet this everyday convenience hides a serious security risk that many businesses overlook.
The problem begins with the fact that autofill does far more than fill in the visible fields on a webpage. When a site requests information, the browser tries to be helpful by supplying as much data as it thinks is relevant. A malicious page can exploit this by embedding invisible form fields that the user cannot see. The page may look like a simple login form with two visible boxes, but in the background it could be silently collecting names, phone numbers, addresses, company details or other sensitive information. The user never notices because the data is filled automatically, without any direct interaction.
This makes autofill a powerful tool for attackers, especially those who build advanced phishing pages. By placing hidden fields behind an otherwise normal-looking form, they trick the browser into revealing much more information than the user intended to share. Even someone who is cautious, who double-checks URLs and avoids suspicious downloads, can unintentionally leak business data simply by loading a compromised page.
The risk increases significantly when employees use the same browser for personal and business purposes. A worker logs into company platforms during the day, then later browses blogs, forums or shopping sites. If one of those pages is compromised, the browser may automatically hand over business-related details, internal emails or other identifiers. Attackers can then use this information to craft highly targeted phishing campaigns, impersonate staff members or attempt account takeovers that look completely legitimate.
Another hidden danger lies in how browsers store login data. Although modern browsers try to restrict autofilling passwords on untrusted pages, attackers constantly develop new ways to bypass these restrictions. Fake login pages designed to resemble commonly used services can prompt the browser to suggest saved credentials. With a single click, those credentials are handed to the attacker — no typing required.
The greatest challenge is that autofill lulls users into a false sense of security. Because information appears automatically, employees pay less attention to the pages they interact with. It becomes easy to overlook subtle differences in layout, URL or domain structure. Familiarity breeds trust, and attackers exploit exactly that.
For businesses, controlling autofill behaviour is an essential part of modern security. Sensitive credentials and business-critical logins should be managed through a dedicated password manager rather than the browser’s built-in storage. Autofill for addresses and payment information should be disabled whenever possible, especially on devices used for work. And employees should be trained to recognize that convenience features can sometimes compromise security — not because of user mistakes, but because of how attackers manipulate these systems behind the scenes.
Autofill may seem like a harmless time-saver, but it can quietly reveal far more than intended. In an environment where attackers depend on subtlety and stealth, limiting autofill is a simple way to prevent invisible data leakage and protect the identity and integrity of your business.
7. Your Browser Stores More Sensitive Data Than You Think
Many business owners imagine that the most sensitive information inside their company lives in cloud systems, databases or internal servers. What often goes unnoticed is that a large portion of this data passes through — and is stored directly inside — the browser. Modern browsers have evolved far beyond simple tools for viewing websites. They act as personal assistants, identity managers and data repositories, quietly collecting information to streamline daily work. And while this makes tasks faster and more convenient, it also creates an unexpected vulnerability that attackers are eager to exploit.
A browser typically holds far more information than users realize. Saved passwords for email accounts, cloud platforms, banking portals and internal systems often sit unprotected behind a simple device login. Autofill entries store names, addresses, phone numbers and sometimes business identifiers. Session cookies keep employees logged in all day long, allowing attackers to bypass logins entirely if they get hold of them. Browsing history reveals which tools the company uses, which admin dashboards staff access and which suppliers or payment platforms are involved in daily operations. Even cached pages and download histories can expose sensitive fragments of internal documents or recently viewed data.
This collection of information creates an incredibly detailed portrait of how a business operates. To an attacker, the browser becomes a map of the company’s digital structure — what platforms it relies on, which employees have access to what and where potential weaknesses may lie. With access to the browser alone, a cybercriminal can often move deeper into the organization without needing to attack servers or crack encryption. The browser becomes the key that unlocks everything behind it.
What makes this situation even more concerning is that browsers were not designed to function as secure enterprise vaults. Their primary purpose has always been convenience, which means usability often comes before protection. Every “remember me,” every saved password, every autofill entry and every persistent login adds another layer of data that stays stored locally in a way that attackers can harvest if they manage to breach the system.
This is why browser-based breaches frequently escalate far beyond the initial compromise. An attacker who gains access to a browser does not just obtain a single piece of information; they inherit an entire identity. They can step into an employee’s digital footprint with minimal effort, appearing fully legitimate in the eyes of cloud platforms and authentication systems. From there, they can access sensitive files, impersonate staff members, manipulate financial processes or create new backdoors that remain hidden long after the initial breach.
For small and medium-sized businesses, ignoring this risk can be costly. Many companies focus on securing cloud providers but forget that attackers often enter long before they reach the cloud — through the employee’s browser on a laptop or workstation. Without strong browser hygiene, even the best-protected cloud environment can be undermined from the outside.
Strengthening browser security therefore becomes a crucial part of protecting a business. Limiting what the browser stores, avoiding built-in password storage, controlling login behaviour, restricting extensions and teaching employees to treat the browser as a sensitive tool rather than a passive window significantly reduces exposure. When the browser is secured, the digital identity of the business becomes far more resilient.
In a landscape where attackers rely on subtlety and speed, the browser is no longer just a tool — it is one of the most critical assets a business must protect.
How to Protect Your Business Immediately
Securing your browser doesn’t require a large IT team, expensive tools, or complex technical procedures. In fact, strengthening browser security is one of the easiest and most impactful steps a business can take — and many of these improvements can be implemented in less than an hour. The goal is simple: reduce the browser’s attack surface and eliminate the most common entry points attackers use.
Below are five essential measures every business should put in place. Together, they form a strong first line of defense and drastically lower the risk of a browser-based breach.
1. Use a Secure Browser With Strict Tracking Protection
Not all browsers are built the same. Some prioritize convenience and speed, while others place a stronger emphasis on privacy and security. For business environments, tracking protection and script isolation have become critical features, especially as modern websites rely heavily on third-party code.
Brave and Firefox offer built-in protections that block many malicious scripts and trackers right out of the box, reducing exposure to drive-by attacks and tracking-based phishing attempts. Hardened Chrome setups — configured with extensions like uBlock Origin and strict privacy settings — can also be effective, but require more manual configuration.
Choosing a secure browser sets the foundation. Once employees use a browser that automatically blocks high-risk content, the number of potential entry points for attackers drops dramatically.
2. Remove All Unnecessary Extensions
Extensions are one of the most overlooked vulnerabilities in business environments. Every extension you install becomes part of your browser’s internal environment — with the ability to view, modify, or inject data into web pages.
The more extensions you have, the larger the attack surface becomes.
Most businesses find that employees use far more extensions than they actually need. Some are installed for convenience, others out of habit, and many simply because they were suggested in a blog post or video. But each unnecessary extension represents a potential risk, especially if its developers sell the project or push a malicious update later.
The safest approach is simple:
Create a small, approved list of trusted extensions and remove everything else.
This immediately cuts off one of the most common infection routes — and also improves browser performance and stability.
3. Block Scripts and Malicious Ads Before They Even Load
Drive-by infections and malicious redirects often originate from scripts and advertising networks embedded in websites. You don’t need to visit a dangerous site to get infected — a single compromised ad on a legitimate page is sometimes enough. That’s why blocking scripts and ads proactively is an essential layer of defense.
Tools like uBlock Origin or NoScript prevent malicious code from executing in the background. They stop rogue ads, script injections, tracking pixels, cryptojacking modules, and many other hidden threats before they get the chance to load.
For small businesses without IT staff, this is a powerful advantage:
Your browser shields you automatically, without requiring manual decisions from employees. Instead of relying on users to “spot” something suspicious, the browser blocks it by default.
4. Enable Automatic Browser Updates — But Never From Pop-Ups
Browser updates are essential because they patch vulnerabilities attackers actively exploit. A browser that is even two or three versions behind can be an easy target. Enabling automatic updates ensures your team is always protected with the latest security fixes.
However — and this is critical — updates should only be installed through the browser’s internal settings menu, not from websites or pop-ups. Fake update messages have become one of the most common vectors for malware and remote-access tools. They appear convincing, but clicking them installs malicious code instead of real updates.
Teaching employees a simple rule creates a massive safety improvement:
If a website tells you your browser is outdated, ignore it.
Update only through the official browser settings.
This prevents one of the most destructive types of modern cyberattacks.
5. Don’t Store Sensitive Passwords in the Browser
Browsers are convenient, but they are not designed to function as secure vaults for business credentials. When a browser stores passwords, anyone who compromises the device — even briefly — can extract those credentials with automated tools. In some cases, malware can steal them directly from the browser’s memory.
Using a dedicated password manager adds an essential security layer. These tools encrypt passwords, require a master key, and often include breach monitoring, secure sharing options, and built-in MFA support. They also prevent employees from falling into risky habits like reusing passwords or storing them in insecure locations.
Once passwords are moved out of the browser and into a password manager, attackers lose one of their easiest access paths.
Conclusion – How hackers use browsers to hack businesses
Understanding how hackers use browsers to hack businesses is no longer optional — it’s a fundamental part of running a secure modern company. The browser has quietly become the central access point to your digital identity, your customer data, your financial tools, and every cloud service your team relies on. And because the browser is used constantly, attackers know it offers countless opportunities to slip through unnoticed.
The truth is simple:
Your business doesn’t need to make a mistake to become a target. One compromised website, one fake update, one rogue extension, or one leaked session cookie is enough to open the door to a silent breach that looks completely legitimate from the outside.
But the good news is just as clear:
With a few smart changes — a secure browser, controlled extensions, strong blocking tools, safe update habits, and a dedicated password manager — you can eliminate most of these risks in a matter of hours. Small adjustments create massive protection.
Hackers rely on businesses being unaware, overwhelmed, or unprepared.
Once you understand how hackers use browsers to hack businesses, you’re already three steps ahead — and you gain the power to turn your browser from a weak link into one of your strongest security defenses.
Your browser is the gateway to your business.
Protect it, and you protect everything that matters behind it.
This could perhaps also be interesting
The Hidden Dangers of AI Browsers – What You Should Know
The Securest Browser for Your Business in 2026 Is Microsoft Edge
Follow me on Facebook or Tumblr to stay up to date
Connect with me on LinkedIn
This is what collaboration looks like
Take a look at my cybersecurity email coaching
And for even more valuable tips, sign up for my newsletter