Cybersecurity is now a core requirement for businesses. Digital threats continue to grow in scale and sophistication. From ransomware gangs demanding millions to AI-powered phishing emails that are nearly indistinguishable from real messages, the threat landscape has evolved dramatically.
Small and medium-sized businesses (SMBs) and freelancers are particularly exposed. Unlike large enterprises, they often lack dedicated IT teams, large security budgets, or mature defense structures. Attackers are well aware of this — and they actively seek out companies that are easier to breach. The consequences can be severe: financial losses, stolen customer data, reputational damage, regulatory penalties, and in some cases, the inability to continue operating at all.
At the same time, modern businesses rely more than ever on cloud services, SaaS platforms, and remote work environments. While this shift enables flexibility and growth, it also expands the attack surface. A single weak password, a compromised third-party vendor, or an unpatched system can be enough to trigger a full-scale security incident.
The good news is this: cybersecurity does not have to be complex or overwhelming. By understanding the most relevant risks of 2026 and taking focused, practical measures, business owners and freelancers can significantly reduce their exposure. In this article, I’ll break down the biggest cybersecurity threats you need to be aware of — and show you clear, actionable steps to protect your company before attackers strike.

1. Ransomware Still Tops the List
Ransomware has remained the number one cyber threat for years — and in 2026, it continues to pose a serious risk to businesses of all sizes. The basic mechanism is simple but highly effective: attackers gain access to systems, encrypt critical data, and demand a ransom, usually paid in cryptocurrency, to restore access. What makes ransomware particularly dangerous is not only the technical damage, but the intense operational and psychological pressure it creates when business operations suddenly come to a halt.
Modern ransomware attacks are far more organized than in the past. Today’s groups operate like professional criminal enterprises, often using ransomware-as-a-service models that allow affiliates to launch attacks with ready-made tools. Many gangs also rely on double-extortion tactics, stealing sensitive data before encryption and threatening to publish it if the ransom is not paid. This combination of data exposure, business disruption, and reputational risk makes ransomware especially effective against smaller organizations.
Small and medium-sized businesses, freelancers, and startups are frequent targets because they are typically easier to compromise and faster to pressure. Attackers deliberately focus on organizations that often:
-
lack dedicated IT or security teams
-
rely on basic or outdated protection measures
-
cannot afford prolonged system outages
The consequences of a ransomware incident can be severe. A design agency may lose access to all client projects overnight, while a freelancer might find their primary work device completely locked, unable to deliver ongoing assignments. Beyond immediate financial losses, ransomware attacks often result in reputational damage, loss of client trust, and long-term business disruption.
Reducing the risk of ransomware requires preparation, technical safeguards, and continuous awareness. Some of the most effective protective measures include:
-
maintaining reliable, regularly tested backups stored offline or in secure cloud environments
-
keeping operating systems, applications, and plugins fully patched
-
staying vigilant with emails, attachments, and links, as many attacks begin with a single click
-
limiting user access based on the principle of least privilege
-
having a clear incident response plan in place before an attack occurs
In 2026, ransomware is no longer an unlikely worst-case scenario — it is a realistic and persistent business risk. Organizations that invest early in preparation and clear security processes are far better positioned to withstand an attack calmly and recover without lasting damage.
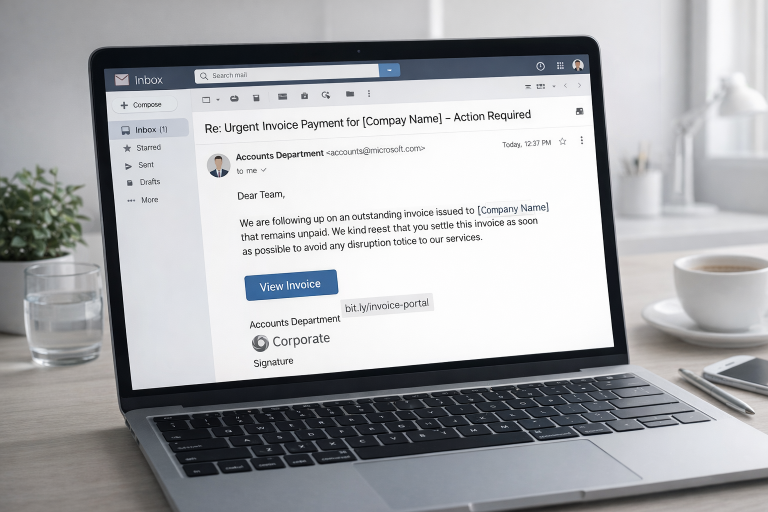
2. Smarter, AI-Powered Phishing
Phishing may sound like an old and familiar threat, but in 2026 it has become more dangerous than ever. The core idea remains the same: attackers try to trick people into clicking malicious links, opening infected attachments, or handing over sensitive information. What has changed dramatically is the level of sophistication behind these attacks, largely driven by artificial intelligence.
In the past, phishing emails were often easy to identify due to spelling mistakes, awkward phrasing, or generic content. Today, AI allows attackers to generate highly convincing messages in multiple languages, carefully tailored to specific roles, industries, and communication styles. These messages closely imitate the tone, layout, and branding of legitimate companies, making them difficult to distinguish from real business communication — even for experienced professionals.
Phishing is also no longer limited to email alone. Attackers increasingly use multiple channels to appear more credible and create pressure, including:
-
SMS messages with fake delivery updates or banking alerts
-
Phone calls from criminals posing as IT support, accountants, or authorities
-
Fraudulent messages via LinkedIn, Slack, Microsoft Teams, or similar platforms
As a result, many scenarios that once seemed unlikely have become routine. Business owners receive emails that appear to come from their bank, warning of suspicious account activity and urging immediate action. Freelancers receive messages that look as if they were sent by trusted clients, asking them to urgently review a document or log in to a shared platform. These attacks are no longer rare — they are part of everyday business life.
Small and medium-sized businesses and freelancers are particularly vulnerable because they operate under constant time pressure and handle large volumes of communication. In such environments, a single distracted moment can be enough to compromise an entire system. Attackers exploit this reality, knowing that smaller organizations often lack strict verification processes or formal approval workflows.
The impact of a successful phishing attack can vary, but often includes:
-
Unauthorized payments or financial fraud
-
Stolen login credentials and exposed client data
-
Malware infections that lead to ransomware or further compromise
Reducing the risk of AI-powered phishing requires a combination of technical controls and behavioral awareness. Enabling multi-factor authentication significantly limits the damage of stolen passwords. Verifying unusual requests through a second communication channel helps prevent manipulation, while regular awareness training keeps phishing risks visible. Modern email and security filters add another layer of protection by blocking many attacks before they ever reach the inbox.
Perhaps most importantly, slowing down is a powerful defense. Messages that rely on urgency or fear are designed to bypass rational thinking. In 2026, effective phishing defense is less about spotting obvious mistakes and more about building habits that prioritize verification over speed.
3. Supply Chain Attacks on the Rise
Supply chain attacks are one of the most underestimated cybersecurity risks — and in 2026, they continue to rise sharply. Instead of attacking a business directly, cybercriminals target the software, tools, service providers, or external partners that a company relies on. Once one of these third parties is compromised, attackers can quietly move “up the chain” and gain access to multiple businesses at once.
Modern companies operate in complex digital ecosystems. Cloud services, SaaS platforms, website plugins, payment providers, and external freelancers are deeply integrated into daily operations. Each connection represents a potential entry point. Attackers know that it is often far easier to compromise a smaller vendor or poorly secured tool than to break through a well-protected company network.
Typical supply chain attack scenarios include:
-
Compromised software updates: Malicious code is injected into a legitimate update and automatically distributed to thousands of users.
-
Breached third-party services: A file-sharing platform, CRM, or marketing tool is hacked, exposing customer or business data.
-
Infected contractor devices: A freelancer’s laptop is compromised, giving attackers indirect access to internal systems.
The underlying problem is simple but dangerous: a business is only as secure as its weakest external dependency.
Small and medium-sized businesses, as well as freelancers, are particularly exposed to supply chain attacks. Large enterprises usually invest heavily in vendor risk management and security audits. Smaller organizations, however, often select tools based on cost, convenience, or speed — not on security maturity. Freelancers may rely on plugins, apps, or sharing platforms without realizing they could become an attack vector for themselves or their clients.
The consequences can escalate quickly. A web designer using a compromised WordPress plugin may unknowingly infect multiple client websites. A small agency relying on a hacked SaaS provider could leak sensitive customer data. A freelancer sharing files through an insecure platform might unintentionally enable ransomware or data theft.
Reducing supply chain risk requires visibility and control. Businesses should work only with trusted providers that demonstrate clear security standards and compliance. External access should be limited to the minimum necessary and revoked as soon as a project ends. Regularly reviewing connected tools, integrations, and permissions helps eliminate unnecessary exposure. Staying informed about security incidents affecting key vendors ensures that potential risks are identified early rather than discovered too late.
In 2026, supply chain security is no longer optional. As businesses become more interconnected, attackers will continue to exploit trust relationships. Organizations that actively manage their digital dependencies are far better positioned to prevent indirect attacks before they turn into full-scale security incidents.
4. Cloud Misconfigurations and SaaS Risks
Cloud services have become the backbone of modern business operations. Whether it’s file storage, collaboration platforms, accounting tools, or industry-specific SaaS solutions, almost every company and freelancer relies on cloud technology to stay productive and competitive. In 2026, this dependency continues to grow — and so does the associated risk.
The biggest danger in cloud environments is often not hacking in the traditional sense, but misconfiguration. In many cases, attackers don’t need to break in at all. They simply scan the internet for exposed storage, weak access controls, or poorly secured cloud accounts. A single mistake can make sensitive business data publicly accessible within seconds.
Common cloud-related security gaps include:
-
Misconfigured storage: Files or databases that are accidentally set to public access.
-
Weak authentication: Reused passwords or missing multi-factor authentication.
-
Excessive permissions: Users, contractors, or apps having more access than necessary.
-
Shadow IT: Employees using unapproved tools outside official oversight.
-
Lingering access: Former employees or freelancers still having active accounts.
Small businesses and freelancers are especially at risk because cloud setup and maintenance is often handled “on the side.” Unlike large enterprises, they usually don’t have cloud security specialists reviewing configurations or monitoring access continuously. Freelancers may manage multiple client accounts at once, increasing the likelihood of overlooked permissions or exposed files.
The consequences range from silent data leaks to compliance violations and, in worst cases, ransomware attacks that originate from cloud accounts. What makes these incidents particularly dangerous is that they often go unnoticed for long periods of time.
Securing cloud environments does not require complexity, but it does require discipline. Enabling multi-factor authentication across all cloud services is one of the most effective protections available. Regularly reviewing access rights, removing unused accounts, and limiting permissions to the minimum necessary significantly reduces exposure. Encrypting sensitive data adds an additional layer of safety, while built-in security dashboards and alerts help detect unusual activity early.
Cloud tools are powerful — but they are not “set and forget.” In 2026, ongoing attention is the difference between flexibility and a serious security incident.
5. AI-Driven Attacks and Deepfake Fraud
Artificial intelligence is transforming business processes — and cybercrime along with them. In 2026, attackers increasingly rely on AI to launch faster, more convincing, and more scalable attacks. What once required skilled teams and weeks of preparation can now be automated and executed at scale.
One of the most alarming developments is the rise of deepfake-based fraud. Using AI-generated voice or video, criminals can convincingly impersonate executives, business partners, or clients. Employees may receive a call that sounds exactly like their manager, urgently requesting a payment or sensitive information. Combined with social engineering, these attacks are highly effective.
AI is also accelerating other forms of cybercrime, including:
-
Highly personalized phishing: AI-generated messages tailored to roles, industries, and individuals.
-
Malware automation: Faster testing and adaptation to bypass security controls.
-
Credential stuffing at scale: Automated attempts using stolen username/password combinations.
-
Behavioral evasion: Attacks that adapt dynamically to security defenses.
Small and medium-sized businesses, as well as freelancers, should be especially cautious. AI lowers the cost of attacks and removes the need for manual effort, meaning that even small organizations become profitable targets. Trust-based workflows, informal communication, and time pressure make these attacks particularly dangerous.
The impact can be immediate and severe. A freelancer might receive a convincing voicemail from a “client” asking to urgently share documents via a link that installs malware. A small finance team may process a payment based on a deepfake call from a “CEO.” An online business could face continuous automated login attempts that disrupt operations and lock out customers.
Defending against AI-driven attacks requires a mix of technology and process. Modern security tools increasingly use machine learning to detect unusual behavior and block threats in real time. Just as important is strict identity verification. Unusual requests involving money, data, or access should always be confirmed through a second channel. Zero-trust principles help ensure that no communication or access request is trusted automatically — even if it appears internal.
Training and awareness are critical. Teams must understand that voice, video, and written messages can all be manipulated. In 2026, relying on intuition alone is no longer sufficient. Regular updates, clear procedures, and a healthy level of skepticism form the most reliable defense against AI-powered cyber threats.
Conclusion: How to Protect Your Business from Ransomware in 2026
Ransomware remains one of the most serious cybersecurity threats in 2026 — but it does not have to cripple your business. The decisive factor is preparation. Companies that invest in reliable backups, strong password policies, multi-factor authentication, and well-defined access controls drastically reduce their risk. Just as critical is awareness: every employee, contractor, and freelancer must be able to recognize suspicious emails, unexpected attachments, and artificial urgency — especially in an age of AI-driven social engineering.
Attackers continue to evolve, but so can your defenses. When cybersecurity is treated as a core part of your business strategy rather than an afterthought, you protect far more than systems and data. You protect your reputation, your customer relationships, and your ability to operate without disruption.
The bottom line: Proactive security measures, continuous training, and the use of modern security tools are the most effective answers to the question of how to protect your business from ransomware in 2026.
In a digitally connected world where threats change rapidly, staying informed and prepared is invaluable. Keep up with security trends, review your defenses regularly, and seek expert guidance when needed. Every step you take today strengthens the long-term resilience and future stability of your business.
I also recommend you read the following articles
Cyberattack Emergency Plan – What to Do When It Happens
Exposing phishing emails: How to recognize fraud attempts – safely and systematically
I’m Too Small to Be a Hacker” – The Most Expensive Mistake in the Middle Class
Is Windows Defender 2025 still the best protection?
The Truth About Password Managers: Security Requires More Than a Tool
Connect with me on LinkedIn
This is what collaboration looks like
Take a look at my cybersecurity email coaching
And for even more valuable tips, sign up for my newsletter