In today’s connected workplace, every employee, from the front desk to top management, plays a crucial role in keeping company data safe. Attackers no longer just target systems; they target people — through deceptive emails, fake login pages, or even casual conversations that reveal more than they should.
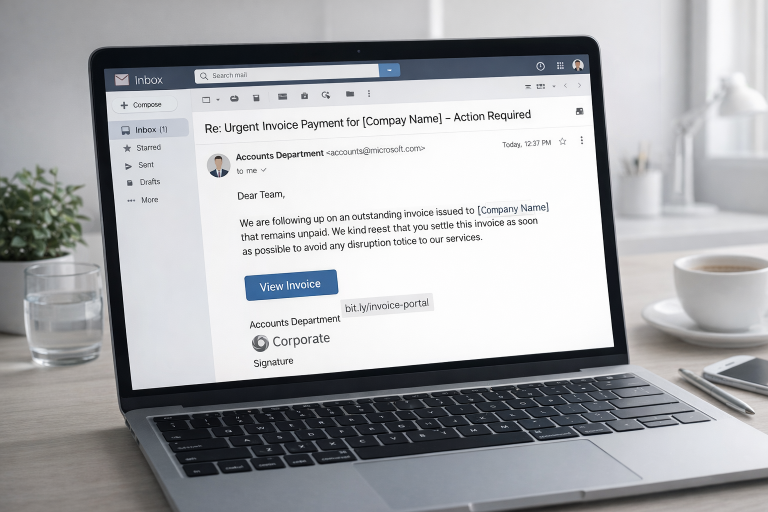
Imagine this: you’re starting your workday, checking emails with a cup of coffee in hand. One message catches your eye — it looks like it’s from your manager, urgently asking for an invoice to be paid. The logo looks real, the tone seems professional… but one wrong click could cost your company thousands of dollars.
That’s how quickly a data breach can begin — not with a hacker breaking through firewalls, but with a single click from an unsuspecting employee.
The good news? Preventing these incidents doesn’t require complex tools or expensive software. It starts with awareness and simple daily habits that build a stronger security culture from the inside out.
Here are five simple but powerful security habits every employee should know — and practice every single day.
1. Think Before You Click
Phishing emails remain one of the most effective and dangerous ways for attackers to infiltrate organizations — not because they use advanced hacking tools, but because they exploit something far more powerful: human behavior.
Most people receive dozens of emails every day, and in the rush of meetings, deadlines, and constant notifications, it’s easy to overlook the small details that separate a legitimate message from a malicious one. Cybercriminals count on that moment of distraction. They know employees are multitasking, often skimming through messages, and that’s exactly when a convincing fake can slip through.
A phishing email doesn’t always look suspicious. In fact, many are crafted to mimic real corporate communication with perfect branding, professional language, and even genuine-looking signatures. Some attackers go further, researching a company’s internal structure to imitate a colleague or manager. You might see a message that appears to come from your HR department asking you to confirm personal details, or from your IT team requesting an urgent password reset. Others pretend to be well-known services like Microsoft, PayPal, or Amazon, claiming that your account will be locked unless you act immediately.
That sense of urgency — the pressure to respond quickly — is what makes phishing so successful.
When we feel stressed or fearful of losing access, we tend to react automatically instead of analyzing the situation.
Yet that one impulsive click can have serious consequences: it can install malware, open a backdoor for remote access, or silently harvest your login credentials. In many cases, the victim doesn’t even realize something has happened until the damage is done.
The best defense is simple: slow down.
Before you click, take a short moment to examine the message carefully. Look at the sender’s address — is it truly from the domain you expect, or does it contain subtle differences, such as extra letters or unusual endings? Read the wording — does it sound natural for that person or company? Are there small grammar or formatting errors that wouldn’t appear in an official email? And most importantly, does the message try to create fear, urgency, or secrecy?
If anything feels slightly “off,” trust your instincts.
Hover over any links to see the real destination before clicking, and never open attachments unless you were expecting them. When uncertain, don’t reply to the suspicious message — instead, report it immediately to your IT or security department. Taking one extra minute to verify can save hours or even days of recovery work later.
2. Use Strong, Unique Passwords
Weak passwords remain one of the easiest ways for cybercriminals to gain access to company systems. A simple combination like Password123 or a birthday may seem harmless, but for an attacker using automated cracking tools, it’s as good as leaving the door unlocked. In fact, common passwords can be cracked within seconds by programs that test millions of combinations per second. These attacks don’t require special genius — just automation and patience. The real vulnerability lies in our human tendency to reuse simple, predictable passwords across multiple accounts.
Hackers exploit this pattern through techniques such as brute force attacks, where software tries every possible combination until it succeeds, or dictionary attacks that rely on common words and predictable phrases. More dangerous still is credential stuffing — a method where cybercriminals take stolen login details from one data breach and test them on other platforms. If you use the same password for your work email, social media, and bank account, one leak can compromise them all.
The foundation of good password security is not complexity for complexity’s sake — it’s uniqueness and length. A strong password should be at least twelve characters long, ideally more, and should mix uppercase and lowercase letters, numbers, and special symbols. But even more important is unpredictability. Avoid personal information like names, addresses, or birthdays, and don’t rely on easy patterns such as “qwerty,” “123456,” or predictable substitutions like “P@ssw0rd.” These tricks have been part of hackers’ dictionaries for years.
One of the simplest ways to create strong but memorable passwords is to use a passphrase instead of a random string of characters. Imagine a short, personal sentence that only you would think of — something like “My cat Phoenix knocked over 7 plants last Tuesday!” If the system allows it, using the entire sentence is ideal. If not, you can take the first letter of each word and mix in symbols or numbers to create a password that’s both unique and strong. Passphrases are easier to remember and much harder for automated tools to crack.
Of course, remembering dozens of unique passwords for every account is nearly impossible, which is why password managers are no longer optional — they’re essential. These tools store and encrypt all your passwords in one secure vault, protected by a single, strong master password. They can automatically generate complex passwords for you, fill them in when needed, and even alert you if one of your accounts has been compromised in a known breach. Instead of reusing weak passwords, you can let your password manager handle the complexity while you focus on your work.
Most reputable password managers — such as Bitwarden, 1Password, Dashlane, or Keeper — are built with zero-knowledge encryption. This means even the service provider cannot see your passwords. The data is encrypted on your device before it’s ever stored in the cloud. For organizations, enterprise solutions like 1Password Business or Dashlane Business allow IT teams to enforce strong password policies while keeping employee credentials safe and easy to manage. Even browser-based managers like those built into Chrome or Safari are better than reusing the same password across multiple accounts.
If you’re getting started, begin with one tool and create a master password that’s both long and memorable — something you can recall but that no one could guess. Then gradually import your existing passwords or let the manager generate new ones as you log in to your accounts. You don’t have to fix everything in one day. Start with your most critical logins — email, banking, and work-related systems — and update the rest over time.
Adding multi-factor authentication (MFA) on top of your password manager gives you another layer of protection. Even if someone steals your master password, they can’t access your vault without the second verification factor, such as a code from an authenticator app or a biometric scan.
Many people worry about “putting all their passwords in one place,” but in reality, password managers use military-grade encryption that makes them far safer than sticky notes, spreadsheets, or memory alone. The biggest mistake isn’t trusting a secure tool — it’s continuing to reuse weak passwords out of convenience.
Strong password habits take time to build, but even small steps make a big difference. Start today by setting up a password manager, updating your three most important account passwords, and enabling MFA wherever possible. Within a few weeks, you’ll have transformed one of the weakest links in your security chain into a solid defense.
Your password is often the only thing standing between an attacker and your company’s sensitive data. Making it strong, unique, and protected isn’t a technical chore — it’s an act of responsibility. In the world of cybersecurity, a good password is your first and most personal firewall.
3. Enable Multi-Factor Authentication
Even the strongest password can be stolen. A well-crafted phishing email, an unnoticed malware infection, or a breach at another service can quietly expose your credentials without you realizing it. That’s why Multi-Factor Authentication (MFA) has become one of the most reliable and cost-effective ways to stop attackers before they gain access. MFA adds an extra layer of security by requiring users to verify their identity in two or more ways — for example, entering a code from an authenticator app, confirming a push notification on a smartphone, or using a physical security key.
Think of MFA as an additional lock on your digital front door. Even if someone has stolen your key — your password — they still can’t walk in without the second factor. This second verification step is what breaks most attack chains. According to Microsoft’s research, MFA can prevent over 99 % of automated account-takeover attempts, simply because attackers can’t generate or intercept that second code fast enough.
In practice, MFA comes in several forms, each with different levels of protection. The most common is the SMS code, where a verification number is sent to your phone. It’s certainly better than nothing, but it’s also vulnerable to SIM-swapping and text message interception. A more secure and convenient option is using an authenticator app, such as Microsoft Authenticator, Google Authenticator, or Authy. These apps generate time-based one-time passwords (TOTPs) that refresh every 30 seconds and don’t rely on your mobile carrier. For the highest level of security, especially for administrators or anyone handling sensitive systems, hardware security keys like YubiKey or Titan Key are the gold standard. They’re physical devices that must be present during login, making remote attacks nearly impossible.
Implementing MFA across a company doesn’t require expensive infrastructure. Most major business tools — from Microsoft 365 and Google Workspace to Slack, Dropbox, and cloud storage providers — already include MFA as a built-in feature. The challenge isn’t technical; it’s behavioral. Employees need to understand why enabling MFA matters and how it protects not just the company, but their own data as well. A short internal awareness session or a clear step-by-step guide can often raise adoption rates dramatically.
In everyday work, MFA becomes second nature. Logging in might take a few seconds longer, but those few seconds could be the difference between a normal day and a full-scale security incident. Attackers often act fast once they steal credentials, trying to access as many systems as possible before being noticed. With MFA in place, their attempts fail instantly because they cannot verify that second factor.
To strengthen your organization’s defenses, enable MFA on all critical systems — company email, cloud platforms, communication tools, and any application handling sensitive data. Encourage employees to prefer authenticator apps over SMS whenever possible, and remind them to never approve a login notification they didn’t initiate. If someone receives a suspicious MFA prompt out of nowhere, it could mean an attacker is trying to access their account — and that should be reported to IT immediately.
For high-privilege users such as administrators, finance staff, or executives, combining MFA with hardware keys provides an additional safety net. These keys are easy to carry, quick to use, and nearly impossible for hackers to bypass.
Ultimately, MFA is one of the simplest yet most powerful habits employees can adopt. It might add a few moments to your login routine, but those moments can save entire days — or even weeks — of recovery after a breach. In cybersecurity, convenience should never outweigh protection. By taking this small extra step, you make life significantly harder for attackers and a lot safer for yourself, your colleagues, and your company.
4. Lock Your Devices When Away
In many offices, cybersecurity feels like something that happens only in the digital world — inside firewalls, passwords, and cloud platforms. Yet one of the simplest and most overlooked risks lies in the physical environment: an unlocked device left unattended. It might seem harmless to leave your laptop open while you grab a coffee or step into a quick meeting, but those few minutes can be all it takes for someone to access sensitive information, copy files, or even install malicious software.
This kind of threat doesn’t just exist in large companies or high-security sectors. It can happen anywhere — in coworking spaces, at conferences, during client visits, or even at home if multiple people share the same environment. A visitor, a curious passerby, or even a cleaning contractor could unintentionally (or intentionally) see information they shouldn’t. And in remote work settings, family members or friends might accidentally click on confidential documents or emails while using your computer.
Locking your screen whenever you step away from your desk is one of the easiest yet most effective security habits you can develop. It’s the digital equivalent of closing the front door when you leave the house. The action takes less than a second — pressing Windows + L on Windows or Control + Command + Q on macOS — but it prevents a world of potential problems. Once locked, your system requires your password, PIN, or biometric verification to reopen, ensuring that only you can continue where you left off.
Beyond manual locking, every employee should enable automatic screen locks after a few minutes of inactivity. This serves as a safety net for the moments you forget to lock manually. Modern devices even allow for smart options such as proximity sensors or Bluetooth-based auto-lock features, which detect when you step away from your workstation.
In open office layouts or shared environments, visual privacy matters just as much. Sensitive information displayed on your screen — customer details, invoices, or internal messages — can easily be seen by others. Privacy screens that limit viewing angles are an inexpensive but powerful way to protect on-screen data, especially for those working with confidential material or in public spaces.
The same principle applies to smartphones and tablets. Always keep them protected with strong passcodes or biometric authentication. It’s easy to underestimate how much sensitive information lives on a mobile device — from company emails and cloud storage apps to saved login sessions and MFA tools. A lost or stolen phone without a lock screen is an open door to your digital life.
Adopting this simple habit sends a powerful message to your team: security isn’t just about technology, it’s about personal responsibility. Each time you lock your device, you reinforce a security-first culture within your workplace — one that values awareness, accountability, and trust.
Cybersecurity doesn’t only happen online. It happens in the small, mindful moments throughout the day — when you pause to verify an email, when you use a password manager, and when you lock your screen before walking away. These actions might seem small, but together, they create a powerful defense against both digital and physical threats.
Remember: One quick keyboard shortcut can prevent an entire security incident. It’s a habit worth building — and one that keeps your organization safe, one locked screen at a time.
5. Stay Alert and Report Suspicious Activity
Cybersecurity awareness isn’t about fear — it’s about attention. Many cyber incidents don’t begin with sophisticated malware or zero-day exploits; they start with something subtle, a small sign that something isn’t quite right. Maybe an employee notices a strange email that doesn’t match a colleague’s usual tone. Maybe someone sees a login alert from an unfamiliar location or a pop-up they’ve never seen before. These small warning signs are often the first indicators of a larger problem, and how quickly they’re recognized and reported can make all the difference.
The truth is that many employees hesitate to report unusual activity. Some assume it’s just a glitch or worry they’ll bother the IT team unnecessarily. But in cybersecurity, silence is often more dangerous than false alarms. What seems like a harmless quirk could be the first step of a phishing campaign, a compromised account, or a ransomware attempt quietly spreading through the network. Early reporting allows security teams to contain issues before they escalate — sometimes within minutes.
Being alert means staying mindful of your digital surroundings. Take note of small irregularities: an unexpected password reset email, a new login prompt on a service you use daily, a colleague asking for information through an unofficial channel, or files behaving strangely after a download. Even slow performance, unusual pop-ups, or system crashes can be signs of an underlying issue. When something feels off, trust that instinct — it’s often your best defense.
Reporting suspicious activity should never feel like an accusation or a burden. It’s part of being a responsible member of a digital workplace. Most companies now have simple, streamlined processes for doing so — a dedicated email address like security@company.com, a helpdesk form, or even a quick chat message to the IT team. The key is speed: the sooner an incident is reported, the faster it can be investigated and resolved. Providing small details, such as timestamps, screenshots, or exact error messages, can give the security team valuable clues to act on.
In a healthy security culture, awareness and communication go hand in hand. Teams that feel empowered to speak up build resilience across the entire organization. When one employee reports something suspicious, it often protects dozens of others who might have been targeted next. This shared responsibility transforms individual caution into collective defense — what experts call the “human firewall.”
Of course, staying alert doesn’t mean living in constant suspicion. It’s about developing quiet awareness — a readiness to notice when something doesn’t match your normal workflow. Over time, this awareness becomes second nature. You begin to spot fake emails faster, recognize legitimate system behavior, and instinctively question unusual requests.
To build this mindset across a company, leaders can encourage a no-blame culture around reporting. Mistakes happen — someone might click the wrong link or download an attachment without checking. What matters most is that they report it quickly. Blame discourages openness; support strengthens security. By celebrating awareness instead of punishing errors, organizations turn lessons into protection.
Staying alert and reporting suspicious activity might sound simple, but it’s one of the most effective habits in modern cybersecurity. Every successful breach that gets stopped in time starts with someone paying attention. Whether you’re in finance, marketing, HR, or IT, your awareness matters. The moment you choose to act — to speak up, to ask, to report — you become part of your company’s strongest defense.
Conclusion: 5 Simple Cybersecurity Habits for Employees
Cybersecurity does not need to be complicated — it only needs to be part of your daily routine.
By following these five simple cybersecurity habits, your company can build a safe and responsible work culture where security becomes something everyone does naturally.
Good security starts with awareness: thinking before you click, using strong passwords, turning on multi-factor authentication, locking your computer when you walk away, and reporting anything that looks suspicious. These small actions make a big difference when they are done every day.
Technology can help protect your systems, but it cannot replace careful people. Real security comes from employees who stay alert and take responsibility. When everyone does their part, the whole company becomes safer — and everyone can work with more confidence and trust.
Please also read:
5 Cybersecurity Myths That Put You at Risk – And How to Stay Safe Online
Cybersecurity 2025: The Biggest Risks for Businesses – and How to Protect Your Company
How to create secure passwords that are extremely difficult to crack
Follow me on Facebook or Tumblr to stay up to date
Connect with me on LinkedIn
This is what collaboration looks like
Take a look at my cybersecurity email coaching
And for even more valuable tips, sign up for my newsletter