Artificial intelligence has become the most dangerous double-edged sword of the digital age. What once required entire criminal networks can now be done by a single person with a laptop, a cloned voice, and an AI model. In 2025, scams are no longer sloppy or obvious — they are fast, personal, and alarmingly convincing. From fake CEO video calls to phishing messages written in your exact tone of voice, AI has transformed deception into a precision weapon. This isn’t just about stolen money anymore. It’s about trust, reputation, and the manipulation of human decisions at scale.
Entrepreneurs, freelancers, and small business owners are especially vulnerable. You move fast, rely on digital communication, and make independent decisions — strengths that scammers now actively exploit. The good news? Awareness still works. If you understand how AI-driven scams operate and learn to recognize the subtle red flags, you can protect your business, your credibility, and your customer trust.
In this article, we’ll break down the five most dangerous AI-powered scams of 2026 — and I show you this how to stay one step ahead.
1. Deepfake Executive Impersonation – When AI Imitates the Boss
Not long ago, deepfakes were little more than internet gimmicks — amusing celebrity edits or political satire. By 2025, they had crossed a decisive line. What was once entertainment has become a serious and highly effective business threat. Modern generative AI allows attackers to create ultra-realistic video and audio impersonations of executives with disturbing accuracy. A few seconds of recorded speech — taken from a podcast, a YouTube interview, a conference clip, or even a voice message — are enough to replicate tone, accent, facial expressions, and mannerisms.
The attack usually feels ordinary. You receive a short video call from your CEO. The voice sounds right. The background looks familiar. She thanks you for your work and then calmly asks you to process a confidential transfer for a partner company before the end of the day. There’s no shouting, no drama — just quiet authority and urgency. You act quickly, because that’s what professionals do. Except the CEO was never there.
The call was an AI-generated deepfake, designed to exploit one of the strongest instincts in any organization: obedience to authority. When instructions appear to come from the top, especially under time pressure, hesitation feels like incompetence. Deepfake scams weaponize that reflex.
This is why these attacks work so well. They don’t rely on technical flaws alone — they exploit psychology. Familiar voices, recognizable faces, and subtle urgency combine into a scenario where even experienced employees suspend doubt. And while large corporations make headlines, small businesses and startups are often even more exposed. Flatter hierarchies, informal communication, and fewer verification layers create exactly the environment attackers are looking for.
Throughout 2025, real-world cases showed how damaging these attacks can be. Finance managers transferred tens of thousands of euros after receiving what appeared to be legitimate video instructions from executives. Suppliers released sensitive contracts after hearing a familiar voice request “just one quick favor.” Many of these deepfakes were produced using freely available or low-cost AI tools, making them faster to deploy and harder to distinguish from reality.
Despite rapid advances in AI, deepfakes still leave subtle traces — if people are trained to notice them. Slight inconsistencies in facial movement, unnatural smoothness in speech, or lighting that doesn’t quite match can be warning signs. More often, the red flags are contextual rather than technical: unusual secrecy, pressure to bypass normal processes, or payment requests that don’t align with current projects. A common tactic is to block verification altogether — claiming there’s no time for calls, emails, or second opinions.
The most effective defense starts with process, not panic. Clear verification rules for financial transactions, multi-person approval thresholds, and mandatory confirmation through known channels dramatically reduce risk. Regular awareness training and short scenario-based exercises help teams recognize manipulation patterns before urgency takes over. Limiting unnecessary public exposure of executive audio and video reduces the raw material attackers can use. Where possible, AI-based detection tools can add an extra layer by analyzing speech patterns, facial movement, and metadata.
Deepfake executive impersonation is no longer a futuristic threat — it’s a boardroom reality. As AI tools become more accessible, imitation will only get easier. But awareness scales too. In the end, the strongest defense isn’t perfect technology. It’s a company culture that values verification over blind compliance — and understands that even the most familiar face can now be an illusion.
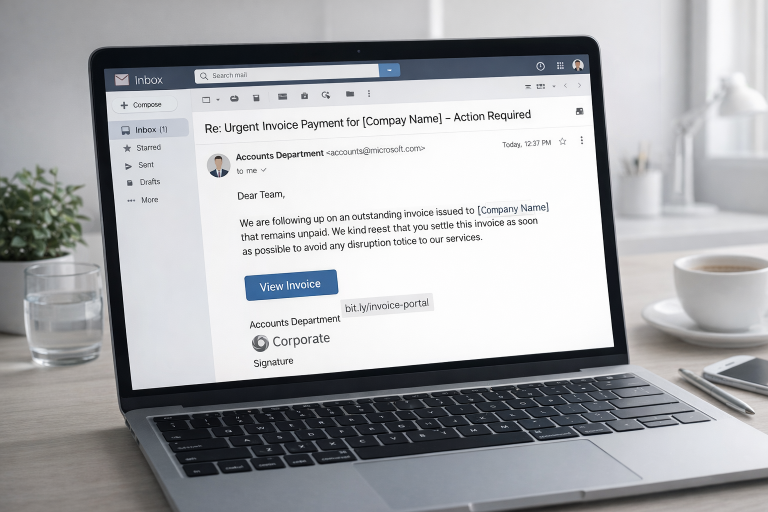
2. AI-Generated Phishing & Conversational Phishing – When the Email Knows You Too Well
If you still imagine phishing as poorly written emails full of typos and obvious red flags, that picture is outdated. By 2026, phishing has become intelligent, adaptive, and highly personalized. Scammers now use large language models to generate messages that sound natural, professional, and disturbingly familiar — often matching your tone, your role, and your business context.
AI-driven phishing is no longer about sending millions of random emails and hoping someone clicks. It’s about precision. Attackers feed public information into AI systems: LinkedIn profiles, company websites, press releases, even old blog posts or job ads. Within seconds, the AI produces a message that looks like it came from your bank, your hosting provider, a business partner, or a colleague.
In many cases, the attack doesn’t stop at a single message. Conversational phishing turns the scam into an ongoing interaction. The AI responds to your replies, mirrors your communication style, and builds trust step by step. Only later does it introduce the actual threat — a malicious link, a “routine” document to review, or a request for login credentials or payment approval.
This type of phishing is exploding because it’s easy to execute, fueled by the massive amount of public data businesses leave online, and perfectly adapted to how entrepreneurs work. When you process dozens or hundreds of messages per day, urgency and familiarity are powerful tools. AI knows exactly how to exploit both.
A typical scenario looks harmless at first. You receive an email that appears to come from your hosting provider. The branding looks right. The domain looks almost identical. The tone matches previous support emails. You’re warned that your SSL certificate will expire within 24 hours and asked to “renew now.” You click, log in — and nothing seems wrong. Hours later, client websites go offline, credentials are compromised, and attackers are already moving laterally through your systems. The entire chain was automated, timed, and personalized by AI.
Even sophisticated AI phishing still leaves traces — but they’re subtle. Watch for small tone shifts that don’t quite match earlier conversations, sender domains that are almost correct, unexpected file types or shortened links, and above all, artificial urgency. Anything that pressures you to act immediately deserves extra scrutiny.
Defending against this threat requires a mix of technology and mindset. Modern email security solutions like Microsoft Defender 365 or Proofpoint now use behavioral analysis and linguistic patterns to flag suspicious messages that look legitimate on the surface. But tools alone aren’t enough.
Regular phishing simulations and short, repeated awareness training help turn vigilance into habit. Multi-factor authentication across all services ensures that stolen credentials are far less valuable. Password managers such as Bitwarden or 1Password reduce the impact of credential leaks by enforcing unique, strong passwords everywhere.
Most importantly, entrepreneurs need a mindset shift. Falling for phishing is no longer about being careless — it’s about being human in an over-automated environment. The more convincing AI becomes, the more valuable a simple pause grows. If a message makes you feel rushed, pressured, or unusually reassured, stop and verify. Because in 2026, the most dangerous phishing emails aren’t the sloppy ones. They’re the ones that look perfect.
3. Synthetic Identity & Persona Scams – When AI Invents a Perfect Business Partner
Not every scam relies on fake bank emails or deepfake executives. Some attackers take a more patient — and far more dangerous — route: they invent entire people.
Synthetic identities are one of the most underestimated fraud vectors of the AI era. These personas aren’t fully fake. They’re built from fragments of real data — a legitimate-looking company registration number, a scraped résumé, a stolen or AI-generated profile photo — all combined into a coherent, believable digital human.
These personas apply for jobs, pitch partnerships, join communities, and even run online businesses that look completely legitimate. They’re not bots in the traditional sense. They are characters, carefully designed to blend into professional ecosystems and exploit trust over time.
A typical attack unfolds slowly. An AI-generated persona appears online with a polished LinkedIn profile, a professional bio, and consistent posting behavior. Tools like Midjourney or D-ID create realistic faces, while language models generate fluent, context-aware communication. Within days, this “person” exists across platforms — LinkedIn, freelance marketplaces, X — complete with endorsements, interactions, and a believable history.
Trust is built quietly. The persona comments on your posts, shares relevant insights, and behaves exactly like a valuable professional contact. Weeks later, the pitch arrives: a collaboration proposal, an investment opportunity, a software demo, or a consulting offer. The website looks polished. The portfolio checks out. Testimonials feel authentic.
Then comes the extraction. You pay an advance fee, grant access to internal tools, or upload data to a partner portal. Shortly after, the website disappears. The accounts go silent. The persona vanishes — along with your money, data, or credentials.
What makes synthetic identity scams so effective is that they don’t trigger immediate alarm. They exploit a fundamental business instinct: the desire to trust and collaborate. Entrepreneurs thrive on networking, speed, and remote partnerships — especially in tech, crypto, and digital services. Synthetic personas weaponize that openness.
In 2025, investigative journalists uncovered entire AI-generated influencer and consultant networks on LinkedIn and X. Hundreds of profiles — complete with photos, job histories, and engagement — traced back to a single coordinated fraud operation. Some promoted non-existent SaaS tools, others posed as cybersecurity firms or marketing agencies. One U.S. fintech startup reportedly lost over $100,000 in “consulting fees” to a company staffed entirely by synthetic identities — including an AI-driven support chat.
Even the most convincing personas leave traces, if you know where to look. Profiles may appear flawless but shallow, with lots of activity and little real depth. Digital footprints often don’t match claimed experience. Profile photos can look slightly too perfect. Engagement patterns feel generic or unnaturally consistent. References and colleagues lead nowhere once you try to verify them.
Defending against this threat requires slowing down where it matters most. Before entering partnerships or transferring money, verify identities through multiple channels — real-time video calls, voice messages, or independent contact details. Adopt lightweight “Know Your Client” checks, even as a small business. Limit access sharing with new contacts and regularly audit your digital communities. For higher-risk collaborations, identity verification platforms such as ID.me, Veriff, or Persona can add an additional layer of certainty.
AI-generated personas are the new wolves in digital clothing. They don’t just steal money or data — they manufacture trust. And once that trust is breached, the damage goes far beyond a single transaction. In a world where anyone can create a believable “someone,” verification is no longer optional. It’s one of the most valuable assets your business has.
4. AI-Powered Investment & Crypto Scams – When Artificial Intelligence Promises You “Guaranteed” Profit
The combination of artificial intelligence and finance is one of the most powerful narratives of the digital era — and scammers know it. By 2025, so-called “AI trading bots,” “automated crypto advisors,” and “next-generation wealth platforms” have flooded social media, each promising effortless, risk-free profits powered by advanced algorithms.
Most of these platforms don’t exist beyond polished landing pages, animated dashboards, and AI-generated testimonials. What makes them dangerous is not technical sophistication alone, but presentation. These are no longer amateur scams with broken English and suspicious domains. They feature professional branding, simulated live-trading interfaces, real-time market visuals, and even deepfake videos of supposed founders claiming to revolutionize investing.
The hook is psychological precision. Entrepreneurs are drawn to efficiency and automation — and an AI that “trades for you 24/7” fits perfectly into the promise of passive income. Scam platforms reinforce this appeal by mimicking legitimate financial services: fake regulatory numbers, cloned broker layouts, and glowing success stories narrated by synthetic voices. Urgency completes the trap. Countdown timers, private beta access, and “limited investor slots” exploit fear of missing out before rational checks kick in.
Often, the illusion works in stages. You deposit a small amount and see instant “profits” appear in your dashboard. Encouraged by visible gains, you’re nudged to reinvest more. Once larger sums are committed, withdrawals suddenly stall — blamed on “AI optimization,” “liquidity windows,” or “manual verification.” Eventually, the platform disappears.
In 2025, several large-scale cases followed this exact pattern. One widely shared “AI arbitrage” platform attracted thousands through TikTok and Telegram before vanishing with millions in crypto. Another claimed to use advanced predictive analytics for trading, complete with deepfake investors showcasing luxury lifestyles. In reality, the entire operation ran on cloned website templates and simulated data feeds. Victims later discovered that their dashboards were nothing more than animated front ends — no real wallets, no real trades.
Even highly polished AI investment scams still reveal cracks if you look closely. Guaranteed high returns are the most obvious red flag — no legitimate financial product can promise profit without risk. Anonymous or unverifiable teams are another warning sign, as real companies disclose founders, offices, and licenses. Vague or missing regulatory oversight, unclear withdrawal conditions, and excessive buzzwords like “quantum prediction” or “adaptive neural finance” usually indicate marketing smoke rather than substance.
Protecting your capital starts with verification and restraint. Always check how long a domain has existed, whether company details are consistent, and whether founders have a real digital history. Legitimate platforms publish audits, technical explanations, or regulatory documentation — scammers rely on excitement and visuals instead. Diversification and capped exposure limit damage, even if a platform turns out to be fraudulent.
5. Voice Cloning & Emergency Impersonation Scams – When the Voice You Trust Isn’t Real
It often begins with a phone call. You hear the voice of someone you trust — a business partner, a colleague, a family member. Calm, familiar, unmistakable. “I’m in a tight spot. I need you to send an urgent payment before the market closes.” You don’t hesitate. The tone is right. The pauses feel natural. Even the small verbal habits are there. Except it isn’t them.
It’s an AI-generated voice clone, trained on minutes — sometimes seconds — of publicly available audio: a podcast appearance, a Zoom recording, a YouTube interview, even a voicemail greeting. Voice cloning fraud has become one of the most emotionally manipulative scams of the AI era because it doesn’t attack systems. It attacks relationships.
Unlike phishing emails or fake websites, voice cloning bypasses logic and goes straight to instinct. Hearing a trusted voice triggers familiarity and urgency at the same time — a combination that shuts down rational analysis. Scammers design their calls to exploit three emotional levers with surgical precision: urgency, guilt, and fear. The request feels personal, confidential, and time-sensitive. By the time doubt creeps in, the money is gone or sensitive information has already been shared.
In 2025, this scam category surged dramatically. In Europe, fraudsters impersonated high-profile executives — even names like Giorgio Armani appeared in investigative reports — to pressure partners into transferring funds. In the U.S., a mother sent thousands of dollars after hearing what she believed was her son’s panicked voice, generated from a short social media clip. In Germany, small business owners received urgent calls from “long-term suppliers,” requesting immediate invoice payments — the voices matched perfectly.
What makes this trend especially dangerous is accessibility. Voice cloning tools are no longer exotic or restricted. Open-source models and freemium services can produce convincing results with minimal audio input. The barrier to entry is low, and the emotional impact is high.
Even so, cloned voices aren’t flawless. Subtle signs still exist if you know what to listen for. The audio may sound unnaturally clean, lacking background noise or microphone texture. Emotional dynamics can feel off — stress without tension, urgency without real variation. Pacing may be slightly irregular, with odd pauses or flattened intonation. Most telling of all: the caller discourages verification, callbacks, or involving others, insisting on secrecy and immediate action.
Defending against voice cloning requires more than technology — it requires process and mindset. Simple verification habits are powerful. Agreeing on a shared verification question or code phrase with close contacts can stop a scam instantly. Any urgent request should be verified through a second channel: a known phone number, a video call, or an official email thread. One communication line is never enough.
Limiting public voice exposure also matters. Public podcasts, long voice messages, and recorded interviews are valuable training data for attackers. Awareness training for employees, clients, and even family members is critical, because many people still underestimate how easily a voice can be replicated. Where available, modern business phone systems with anomaly detection or voiceprint verification add another layer of defense.
Ultimately, the strongest protection is emotional awareness. Voice cloning works because it creates panic, urgency, or misplaced loyalty. The moment a call makes you feel rushed or alarmed is the moment to pause. These scams expose an uncomfortable truth: familiarity is no longer proof of authenticity. Hearing a trusted voice used to mean safety. In the AI era, it can mean the opposite. This doesn’t require paranoia — it requires evolution. Slowing down. Verifying deliberately. Replacing blind trust with conscious confirmation. Because while technology can now imitate sound perfectly, critical thinking still can’t be cloned.
Conclusion – The Biggest AI Scams of 2026 and How to Protect Your Business
Artificial intelligence has reshaped not only how we work, but how fraud succeeds. The dominant AI scams of 2025 make one thing clear for 2026: attacks no longer target systems first — they target trust. Deepfakes mimic leadership, AI-generated messages imitate trusted partners, and cloned voices exploit our instinct to believe what feels familiar.
For entrepreneurs, this shift requires more than technical defenses. It demands a new mindset. In a world where seeing and hearing are no longer proof, real security begins with slowing down, verifying information, and questioning urgency — because pressure is often the first sign of manipulation.
AI-powered scams will keep evolving. They will become faster, cheaper, and more convincing. But so can human awareness. With clear verification processes, trained teams, and an understanding of emotional triggers, risk can be reduced where it matters most: in moments of stress and rushed decisions.
In the end, cybersecurity in the AI era isn’t about having the most advanced tools. It’s about staying calm, informed, and deliberately skeptical. Because in 2026, the strongest defense your business has isn’t artificial intelligence — it’s human intelligence, used consciously.
I also recommend that you read the following articles
AI-Phishing Emails: Why They’re Harder to Detect Than Ever
Can AI Help Your Company Avoid Hacker Attacks?
Smarter Security: Are AI-Powered Firewalls the Future of Cyber Defense
Follow me on Facebook or Tumblr
to stay up to date.
Connect with me on LinkedIn
Take a look at my services
And for even more valuable tips, sign up for
my newsletter