
All computers locked – what to do in the event of a ransomware attack?
Cordula BoeckImagine this: It’s an ordinary Monday morning. The coffee machine is running, your team is…

What Really Goes Wrong in the First 6 Hours After a Cyberattack
Cordula BoeckWhat happens in the first hours after a cyberattack? Let’s get find out in this…

This is how modern cyberattacks really begin – a look behind the scenes (Part 2 of 4)
Cordula BoeckWelcome back. This is Part 2 of our four-part series on why cyberattacks are successful…
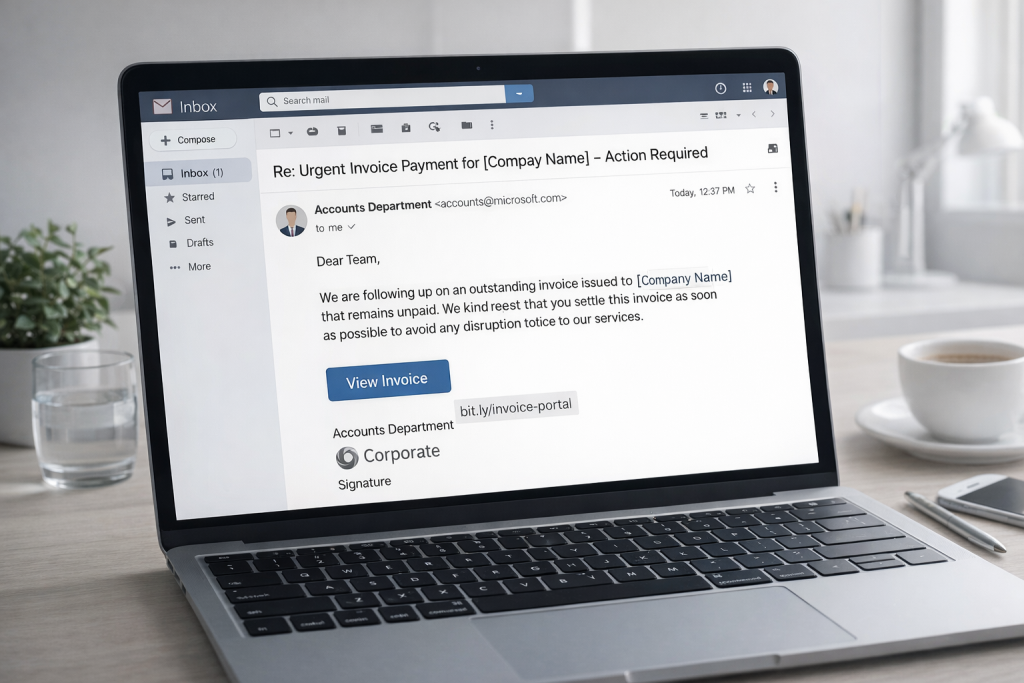
The Components of an Attack: The 7 Phases of a Modern Phishing Attempt
Cordula BoeckPhishing has changed a lot in recent years. What used to be simple, poorly written…

A Practical Cybersecurity Briefing for Business Decision Makers
Cordula BoeckCybersecurity is no longer a purely technical issue. It has become a matter of leadership…

Deepfake fraud in 2026: Why voices and videos can no longer be trusted
Cordula BoeckDeepfakes are no longer a future risk — they are now part of everyday digital…

Why cyberattacks are successful: Understanding the real causes (Part 1 of 4)
Cordula BoeckWelcome to CybersecureGuard Newsletter and 1 of the 4 Articel series. This newsletter is…

Why Immediate System Shutdowns Often Make Ransomware Incidents Worse
Cordula BoeckWhy shutting down systems during ransomware is dangerous, find it out in this articel. When…

The 5 Biggest AI Scams of 2026 — and How Entrepreneurs Can Stay Safe
Cordula BoeckArtificial intelligence has become the most dangerous double-edged sword of the digital age. What once…

Top 6 Password Managers Compared: Which One Keeps You Safest in 2026?
Cordula BoeckIn 2026, relying on a single weak password – or worse, reusing the same one…

Cybersecurity 2026: The Biggest Risks for Businesses – and How to Protect Your Company
Cordula BoeckCybersecurity is now a core requirement for businesses. Digital threats continue to grow in scale…

I’m Too Small to Be a Hacker” – The Most Expensive Mistake in the Middle Class
Cordula BoeckThis sentence is heard surprisingly often in conversations with small and mid-sized business owners. It…

The Truth About Password Managers: Security Requires More Than a Tool
Cordula BoeckPasswords remain one of the most common ways to protect digital systems and business accounts….

How Prepared Is Your Company? A Realistic Cybersecurity Reality Check
Cordula BoeckA new year is a good moment to pause and look at what really matters….

A Secure Closing for Your 2025 – Reflections on Cybersecurity at Year’s End
Cordula BoeckThe final weeks of the year are often calmer. Many projects are coming to an…

When Cyber Insurance Becomes a Dangerous Illusion
Cordula BoeckCyberattacks are no longer a marginal issue affecting only large corporations with dedicated IT departments….

The Truth About Virus Protection on Smartphones – A Reality Check for SMEs
Cordula BoeckSmartphones are no longer private gadgets. For small and medium-sized businesses, they have become core…

How to Build an IT Security Strategy That Actually Works
Cordula BoeckMany companies begin their cybersecurity strategy by investing in tools. Antivirus software, firewalls, cloud security…

The Role of Firewalls in Modern Business Cybersecurity
Cordula BoeckIn modern business environments, cybersecurity is no longer a background IT task. It has become…

Home Office Security for Businesses: How to Protect Remote Employees and Data
Cordula BoeckIn today’s modern professional landscape, the home office has evolved from a flexible perk into…

How SMEs Can Train Employees to Recognize Phishing Attacks
Cordula BoeckPhishing attacks are no longer rare or sophisticated exceptions. They have become one of the…

WordPress Security Vulnerabilities in 2026: The 6 Most Common Risks Businesses Overlook
Cordula BoeckFor many businesses, WordPress security feels under control: the website is online, a basic plugin…

When Outdated IT Becomes a Security Risk – What Your Company Needs to Know
Cordula BoeckIn many organizations, outdated IT devices are not the result of poor planning or negligence.They…

5 Red Flags That Your Business May Already Be in a Hacker’s Crosshairs
Cordula BoeckCyberattacks rarely begin with loud, dramatic failures. In most cases, the first phase is quiet…
8 Real Cyberattack Stories from Germany That Almost Destroyed Businesses
Cordula BoeckCyberattacks in Germany are no longer distant, conceptual dangers; they have evolved into a direct…

The 7 Best Backup Tools for Your Company in 2026
Cordula BoeckReliable data protection is no longer optional — it has become a fundamental requirement for…

The 6 Cyber Threats Every Small Business Must Prepare for in 2026
Cordula BoeckFor years, many small and medium-sized businesses believed they were “too small to hack.” Cybercriminals,…

How to Protect Your Business Wi-Fi Network From Hackers
Cordula BoeckYour office Wi-Fi network is more than a convenience — it is a crucial component…

The Worst Computer Viruses of All Time — and What Your Company Can Learn From Them
Cordula BoeckCyberattacks have evolved enormously over the past decades, yet the core truth behind them has…

How to Protect Your Company’s Mobile Phones and Laptops from Cyber Threats
Cordula BoeckCompany devices today are more than just tools for daily work. They act as digital…

Browser Security Report 2026: How Safe Are Modern Browsers Against Today’s Threats?
Cordula BoeckModern browsers have become the central hub of our digital lives. We use them to…

How to Secure Your Startup from Cyber Attacks: A Practical IT Security Checklist
Cordula BoeckLaunching a startup is an intense and fast-moving journey. During the early months, every founder…

How to Secure Your Business After a Virus Infection on the Network
Cordula BoeckDiscovering a virus on your company network can feel alarming — especially when your business…

Latest AI fraud: How fake emails out of nowhere are putting entire companies at risk
Cordula BoeckArtificial intelligence has become a powerful driver of productivity, innovation, and efficiency in modern organizations….

The Ultimate Backup Guide for Small Businesses in 2026
Cordula BoeckRunning a small business in 2026 means navigating a world where digital risks have grown…

Why a Fake Invoice Can Ruin Your Business – and How to Prevent It
Cordula BoeckWhy a Fake Invoice Can Ruin Your Business, find it out in this article. It…

The Hidden Cost of a Ransomware Attack — And Why It Can Break Your Business
Cordula BoeckRansomware has become the kind of business nightmare nobody wants to talk about — until…

The Hidden Risk: How Hackers Use Your Browser to Breach Your Business
Cordula BoeckFor most small and medium-sized businesses, the real danger begins with something completely ordinary: the…

How to Build a Simple and Effective Cybersecurity Plan for Your Team
Cordula BoeckCybersecurity often feels overwhelming — especially for small businesses. New threats appear every week, tools…

GDPR Made Simple: A Practical Checklist for Small Business Compliance in the UK
Cordula BoeckLet’s be honest: most business owners feel a little tired of hearing about data protection…

How Do I Protect My Small Business From Hacker Attacks?
Cordula BoeckCyberattacks are one of the biggest threats to modern businesses — and small companies are…

Why Small Businesses Can’t Afford Weak Protection in 2026
Cordula BoeckCyberattacks are no longer reserved for big corporations or government networks, small and medium-sized businesses…

The Securest Browser for Your Business in 2026 Is Microsoft Edge
Cordula BoeckYour web browser is one of the most frequently used tools in your business —…

Examples of Phishing Attacks on Small Businesses — And How to Detect Them Early
Cordula BoeckFind out in this article how examples of phishing attacks on small businesses. Phishing is…

5 Simple Security Habits Every Employee Should Know
Cordula BoeckIn today’s connected workplace, every employee, from the front desk to top management, plays a…

Comet Browser under the microscope: What you need to know about data protection with the Comet Browser
Cordula BoeckIs the Comet browser a security risk for your company?, Let’s find out together in…

VPNs for Business: Security Tool or False Sense of Safety?
Cordula BoeckFor many companies, “turn on the VPN” has long meant “we are safe.” But in…

How to Improve Workplace Privacy Without Losing Productivity
Cordula BoeckLearn how to improve workplace privacy without losing productivity. Practical steps to protect your data…

How Small Businesses Can Switch from Passwords to Passkeys – and Why They Should Do It Now
Cordula BoeckFor many years, passwords have been the standard way to protect online accounts. Every employee,…

How Useful Are Security Plugins for WordPress? – An Honest Look Behind the Scenes
Cordula BoeckWhen it comes to protecting your WordPress website, the first thing most people do is…

5 Cybersecurity Myths That Put You at Risk – And How to Stay Safe Online
Cordula BoeckThink you’re safe from hackers? Think again. Today cyberattacks have become an everyday reality. Hackers…
The 10 Best Tips for Windows Defender – Protect Your PC Like a Pro
Cordula BoeckAs cyberattacks become more sophisticated and frequent, one built-in security solution quietly stands guard on…

Windows Defender for Business vs ESET PROTECT Business Comparison Guide
Cordula BoeckWhen companies choose an antivirus or endpoint protection solution, they often compare Microsoft’s Windows Defender…

How to Identify Dangerous Phishing Emails in Your Company
Cordula BoeckFind out in this guide How to Identify Phishing Emails in the Workplace. Phishing remains…

Your Antivirus Sounds the Alarm? Here’s How to Check if It’s Really Dangerous
Cordula BoeckYou’re working quietly, maybe downloading a file or updating a trusted app — when suddenly…
What to Do When Your Business Gets Infected by a Virus — Best Tools to Remove Trojans and Worm
Cordula BoeckImagine this: It’s a regular morning at the office. You grab your coffee, open your…

How Hackers Use Artificial Intelligence Against Businesses — and How You Can Protect Yours
Cordula BoeckArtificial Intelligence has rapidly evolved from a powerful innovation driver into the new frontline…

Backup Strategies with OneDrive: What Happens If Something Is Deleted?
Cordula BoeckMany users rely on Microsoft OneDrive to store and organize their important files — from…

How Hackers Break Into Microsoft 365 — and How You Can Stop Them
Cordula BoeckFind out in this Article How Hackers Break Into Microsoft 365 and how you can…

Social Engineering: How Hackers Trick You in Daily Life
Cordula BoeckDiscover the 5 types of social engineering attacks in this Articel. When people think about…

Ransomware in Small Businesses: 5 Steps You Can Take Right Away
Cordula BoeckImagine starting your workday as usual — you open your laptop, log into your accounting…
Windows Firewall vs. Avira – Which One Protects You Better?
Cordula BoeckWhen it comes to PC security, most people immediately think of antivirus software. But there’s…

Can a PDF File Be Malware? The Hidden Dangers You Need to Know
Cordula BoeckPDF files have become the standard for sharing information across the globe. From digital invoices…

Inside Germany’s Ransomware Struggle: Lessons from Real Incidents
Cordula BoeckRansomware is no longer just a buzzword in the cybersecurity community — it has become…

Can AI Help Your Company Avoid Hacker Attacks?
Cordula BoeckCyberattacks are no longer just a problem for large corporations – small and medium-sized businesses…

The WannaCry Hack: How a Virus Could Spread Worldwide in Hours
Cordula BoeckIn the digital age, we often imagine hackers as shadowy figures working quietly in the…

Cloud vs. On-Premises: Why the Hybrid Approach Is the Best Solution for Businesses
Cordula BoeckWhy hybrid cloud is the best solution for modern businesses, let it find out in…

Airport offline: How vulnerable our systems really are
Cordula BoeckImagine arriving at the airport for an important business trip or long-awaited holiday. Instead of…

Windows 10: Why Sticking With It Is a Security Risk for SMEs
Cordula BoeckAcross offices, workshops, and home offices, Windows 10 is still everywhere. Many small and medium-sized…

Is Antivirus Software Sufficient Protection Against Ransomware? The Shocking Truth for SMEs
Cordula BoeckFor many small and medium-sized enterprises (SMEs), cybersecurity feels like something that only big corporations…

How to create secure passwords that are extremely difficult to crack
Cordula BoeckAlmost every part of daily life is now tied to the internet — from online…

How to Recognize an AI-Generated Phishing Email in Just a Few Seconds
Cordula BoeckPhishing attacks are one of the oldest tricks in the cybercriminal playbook — but lately,…

That’s Why Password Managers Are Not as Secure as You Think
Cordula BoeckWhen it comes to protecting our digital lives, password managers are often presented as the…

How a Single Email Attachment Took Down a WordPress Website
Cordula BoeckCyberattacks often feel like something that only happens to large corporations. We read headlines about…

When does Microsoft Defender Business make sense for you and your company?
Cordula BoeckCyberattacks have become part of everyday business life – whether it’s phishing emails, ransomware, or…

Why Virus Protection Alone Is Rarely Enough – and Why Knowledge Is the Key
Cordula BoeckDiscover in this Articel, why antivirus software alone is not enough for businesses. Learn how…

How to recognize phishing and Trojans – 7 warning signs you need to know
Cordula BoeckPhishing, Trojans, and fake emails—you’ve probably heard these terms before. However, many people underestimate the…

Will your company still need antivirus software in 2025 – or is it just expensive snake oil?
Cordula Boeckhttps://www.youtube.com/watch?v=stgSUnMQJFk&t=374s Cybersecurity is no longer a niche concern – it’s one of the most critical…

Smarter Security: Are AI-Powered Firewalls the Future of Cyber Defense
Cordula BoeckCyberattacks are no longer a rare event but part of everyday life – for businesses…

Darknet Basics: Everything you need to know about the hidden side of the internet
Cordula BoeckThe dark web has exerted an almost mystical fascination for years. Many people only know…

4 top search engines that will make Google look outdated in 2025
Cordula BoeckGoogle is undoubtedly the top dog among search engines—over 90% of all search queries worldwide…

Cyberattack Emergency Plan – What to Do When It Happens
Cordula BoeckIn the last 10 years, cyberattacks have become one of the biggest threats to businesses,…

The Ultimate WordPress Security Guide: Protect Your Website from Threats and Attacks
Cordula BoeckWelcome to the ultimate WordPress security guide — your comprehensive protection against threats and attacks…

AI-Phishing Emails: Why They’re Harder to Detect Than Ever
Cordula BoeckThink of a classic phishing email. Not too hard, right? You’re probably picturing a poorly…

Cloud Security 2025: How Safe Is Your Data?
Cordula BoeckThe cloud has quietly become the backbone of our digital lives. Whether we’re streaming movies…

VPN myths in 2025 – What’s true and what’s not?
Cordula BoeckVPNs have been a hot topic for years—and in 2025, more than ever. Hardly a…
Optimally setting up Windows Defender: Complete guide
Cordula BoeckMicrosoft Defender, formerly known as Windows Defender, has evolved significantly since its launch. From a…

Will Windows Defender still be secure enough in 2026? What businesses should know before relying on it
Cordula BoeckWill Windows Defender still be secure enough in 2026? Many small and medium-sized businesses are…

Exposing phishing emails: How to recognize fraud attempts – safely and systematically
Cordula BoeckYou open your email inbox in the morning – and there it is: a message…
The Hidden Dangers of AI Browsers – What You Should Know
Cordula BoeckIn 2025, artificial intelligence has finally made its way into our browsers. From smart summarization…
