Cyberattacks are one of the biggest threats to modern businesses — and small companies are no exception.
Every day, hackers look for easy targets: businesses with weak passwords, outdated systems, or untrained employees. And because many small businesses think, “We’re too small to be interesting,” they often become the first to be attacked.
A single cyber incident can have devastating consequences. It can lock you out of your systems, leak customer data, damage your reputation, and cost thousands in recovery expenses or legal penalties. According to recent studies, 43% of all cyberattacks target small and medium-sized businesses, yet most of them have no dedicated IT security team in place.
The good news: you don’t need an expensive setup or a large team to stay safe. By following a few practical steps and adopting good security habits, you can protect your business, your clients, and your peace of mind.
1. Why Hackers Target Small Businesses
Many small business owners still believe that cybercriminals only attack large corporations with millions in revenue and hundreds of employees. But in reality, it’s often the opposite. Hackers see small and medium-sized companies as the perfect combination of valuable digital data and weak protection. They know these businesses rarely have dedicated IT security staff, rely on outdated systems, and underestimate their own attractiveness as a target.
For attackers, this creates the ideal situation: low effort, low risk, and a potentially high reward. A small business might store sensitive customer details, payment data, invoices, and passwords — all of which can be sold on the dark web or used for identity theft. Even if the data itself isn’t huge in volume, its quality and freshness make it extremely profitable.
Another key reason is the lack of consistent security updates and employee awareness. Many owners postpone system updates because they fear downtime or compatibility problems, without realising that each skipped update leaves a known vulnerability open. Automated tools constantly scan the internet for exactly these weak points — old WordPress plug-ins, unpatched routers, or misconfigured email servers — and once a flaw is found, the attack often happens within hours.
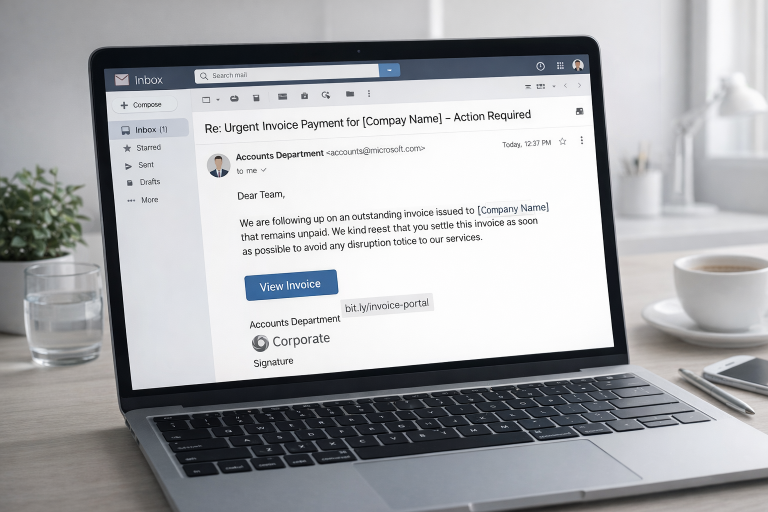
Social engineering also plays a major role. In small teams, where everyone knows each other and communication is informal, it’s easy for an attacker to impersonate a colleague or supplier. A simple email saying “Please pay this invoice today — it’s urgent” can be enough to trigger a costly mistake. Hackers count on human trust and the fact that smaller companies rarely double-check such messages.
Finally, small businesses are often part of a larger supply chain. By compromising a small vendor or service provider, attackers can gain indirect access to the systems of bigger partners. This “side door” method has become one of the most effective strategies in modern cybercrime.
In short, hackers target small businesses because they are easier to break into, slower to detect intrusions, and less likely to involve law enforcement or cybersecurity experts. But this also means that with a few practical improvements — regular updates, employee training, and stronger access control — a small company can quickly move from easy prey to a much harder target.
2. The Most Common Attack Methods
Once you understand why hackers target small businesses, it becomes easier to see how they do it. Most attacks don’t start with complex technical tricks — they begin with human behaviour. A careless click, a weak password, or an outdated system is often all it takes to open the door.
One of the most common threats is phishing. These are deceptive emails that look legitimate — often appearing to come from a trusted source such as a bank, a supplier, or even your own company. The goal is simple: to make you click on a malicious link or open an infected attachment. Once that happens, attackers can steal login credentials, install malware, or trick you into transferring money. Some phishing messages are so convincing that even experienced employees can fall for them if they’re in a hurry.
Another frequent entry point is the use of weak or reused passwords. Many employees still use simple passwords like Welcome123 or repeat the same login across multiple services. Hackers use automated “credential stuffing” tools to test these password combinations on thousands of accounts until they find one that works. With just a single compromised account, they can access emails, invoices, and internal files — sometimes for weeks before being noticed.
Ransomware attacks are particularly damaging. In this scenario, hackers encrypt all your business data and demand a ransom payment to unlock it. Paying the ransom rarely helps — it encourages further attacks and doesn’t guarantee recovery. In most cases, the root cause is outdated or unpatched software that contains known security flaws. Many ransomware infections could be prevented simply by keeping systems and antivirus solutions up to date.
Another silent but dangerous risk comes from unsecured Wi-Fi networks. Many small offices use routers with default passwords or outdated encryption methods. Remote workers often connect from cafés, airports, or home networks that aren’t properly protected. Hackers can intercept traffic on these networks, steal login data, or inject malicious code into legitimate connections.
Sometimes, attackers don’t even need to hack your systems directly. They might compromise your cloud accounts or third-party services — for example, your accounting platform or online store. These platforms can become entry points if you use weak passwords or skip two-factor authentication.
In short, most cyberattacks against small businesses don’t rely on Hollywood-style hacking scenes. They exploit everyday habits: rushing through emails, ignoring updates, reusing passwords, or leaving Wi-Fi unprotected. The more aware you and your team are of these methods, the harder it becomes for attackers to succeed.
3. Five Steps to Protect Your Business
Cybersecurity may sound complicated, but protecting your business doesn’t require a huge budget or a full-time IT department. What matters most is consistency — small, regular actions that close the biggest security gaps. These five steps are simple to apply and can drastically reduce your risk of falling victim to a cyberattack.
1️⃣ Keep your software and devices updated
Updates are your first line of defence. Every update includes security patches that fix known vulnerabilities — the same weaknesses hackers actively look for. Delaying updates, even by a few days, can give attackers an opportunity to exploit your system. Make it a habit to enable automatic updates on all company devices and check regularly that every machine is running the latest version.
2️⃣ Use strong passwords and multi-factor authentication (MFA)
A strong password is like a solid lock — it keeps unwanted visitors out. Use a mix of uppercase and lowercase letters, numbers, and symbols. Never reuse the same password for multiple accounts, and consider using a password manager to keep them secure. Adding MFA (for example, a verification code on your phone) creates an extra barrier that makes it almost impossible for hackers to log in, even if they know your password.
3️⃣ Train your team to spot phishing emails
Human error remains the number one cause of cyber incidents. A single careless click can infect an entire network.
Hold short, regular awareness sessions — even 15 minutes per month — to teach your team how to recognise fake emails, suspicious attachments, and unusual requests. Encourage them to double-check anything that feels “off,” especially messages asking for money transfers or password resets. A culture of awareness is one of the most powerful security tools you can build.
4️⃣ Back up your data regularly
Backups are your safety net. In case of a ransomware attack, hardware failure, or accidental deletion, a recent backup ensures you can recover quickly. Use a combination of local and cloud backups, and make sure one copy is stored offline or in a secure external location. Equally important: test your backups regularly to confirm they can be restored when needed — many businesses forget this step until it’s too late.
5️⃣ Get an external cybersecurity check
Even the most careful business owner can overlook something. That’s why a professional audit is invaluable.
An external cybersecurity check identifies blind spots, outdated settings, or weak configurations that internal teams may miss. It gives you a clear, actionable overview of where your company stands and what needs improvement.
👉 My personalized CybersecureGuard Small Security Audit does exactly that — a practical, 24-hour assessment designed specifically for small businesses.
4. What to Do If Your Company Was Hacked
Even with the best protection in place, no business is completely immune to cyberattacks.
What matters most is how you respond in the first few hours. A calm, structured reaction can make the difference between a minor incident and a full-scale business disaster.
The first step is to stay calm and act quickly. Panic often leads to mistakes that make things worse. Your goal is to contain the attack, limit the damage, and prevent further spread.
1️⃣ Disconnect affected devices
If you suspect that a computer, server, or phone has been infected, disconnect it immediately from the internet and your internal network.
This prevents the attacker from moving laterally — that is, spreading the malware to other systems or stealing more data in real time.
Do not delete or reinstall anything yet. Important forensic information may be lost if you start cleaning too soon.
2️⃣ Don’t pay the ransom
In the case of a ransomware attack, paying the ransom may seem like the fastest way to get your data back. Unfortunately, it rarely works that way. Many victims never receive the promised decryption key, and paying only encourages future attacks — marking your company as an easy target. Instead, focus on restoring systems from clean backups once they’re verified as safe.
3️⃣ Contact a cybersecurity professional
Don’t try to fix everything on your own. A cybersecurity expert can identify how the attacker entered, determine what was affected, and help secure your systems before you bring them back online. They can also assist with legal and reporting obligations, depending on your region’s data protection laws (for example, GDPR in the EU or ICO reporting in the UK).
4️⃣ Restore data from a clean backup
Once the infected systems are isolated and the root cause is fixed, restore your files from a verified backup.
Always double-check that the backup was created before the attack occurred. Bringing back an already infected version can reintroduce the problem.
5️⃣ Learn from the incident
Every attack, even a small one, provides valuable lessons. Review what went wrong — was it a missed update, a weak password, or a lack of staff awareness? Use that insight to strengthen your defences, update your policies, and schedule regular training. The goal isn’t just to recover — it’s to make sure it doesn’t happen again.
Remember: being hacked doesn’t mean you’ve failed. It means you’ve become part of a modern business reality. What separates resilient companies from vulnerable ones is how prepared they are to respond.
5. Protect Your Business Now
Cybersecurity isn’t something to think about after an attack — it’s a continuous habit, just like maintaining your office or updating your accounts. Every company, no matter how small, has something valuable to protect: customer trust, financial data, and the time you’ve invested in building your business.
The truth is, most cyberattacks don’t happen overnight. They start quietly — with a single weak password, an ignored update, or a phishing email that looks harmless. Over time, these small gaps grow into serious vulnerabilities.
That’s why the best time to strengthen your defences is now, before someone else decides to test them.
Start with the basics: review your passwords, update your systems, and make sure your team understands how to spot suspicious messages. Even simple changes can drastically reduce your risk. And if you’re not sure where your weakest points are — that’s where professional guidance can make all the difference.
Conlcusion: how to protect my small business from hackers
Protecting your small business from hackers isn’t about complicated technology — it’s about awareness, consistency, and preparation. The biggest mistakes small companies make are believing they’re too small to be attacked and postponing simple security habits like updates, backups, or staff training.
Cybersecurity is no longer optional. Every password, every update, and every policy you set today becomes a shield against tomorrow’s threats. Even a few small improvements can stop the majority of attacks before they begin.
So if you’ve ever asked yourself, “how to protect my small business from hackers?”, the answer starts with taking small but consistent actions — and getting expert guidance when needed.
At CybersecureGuard, I make cybersecurity simple and practical for small businesses. Start with your Small Business Security Audit today and gain the peace of mind that comes from knowing your business is protected.
👉 Get your audit within 24 hours
Please also read
All computers locked – what to do in the event of a ransomware attack?
Cybersecurity 2025: The Biggest Risks for Businesses – and How to Protect Your Company
How to create secure passwords that are extremely difficult to crack
Ransomware in Small Businesses: 5 Steps You Can Take Right Away
Follow me on Facebook or Tumblr to stay up to date
Connect with me on LinkedIn
This is what collaboration looks like
Take a look at my cybersecurity email coaching
And for even more valuable tips, sign up for my newsletter