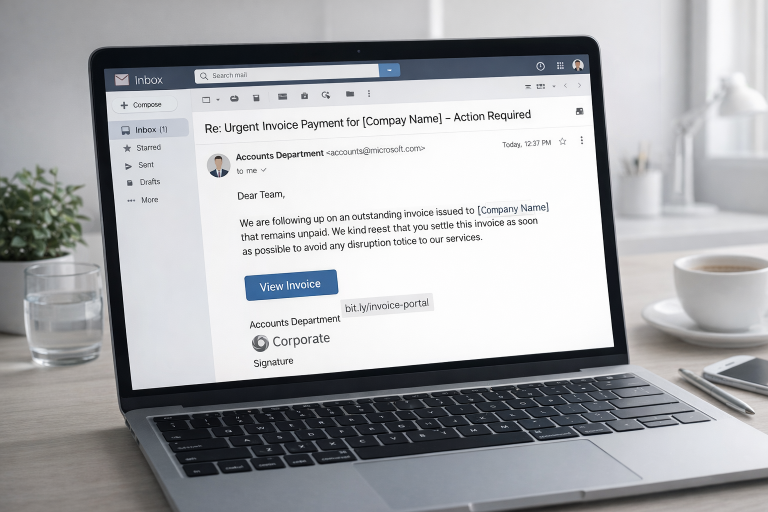
You open your email inbox in the morning – and there it is: a message from your bank, a parcel delivery service, or an online shop.
The subject line reads: “Urgent! Final warning!” or “Your account has been compromised.”
Or maybe the email sounds tempting – “Congratulations, you’ve won!”
But something about it just feels… off.
Welcome to the world of phishing emails and spoofed senders, operating in 2025 more cleverly than ever before.
Cybercriminals use deceptively real logos, manipulated email addresses, and psychological tricks to get their hands on your data or money.
But don’t worry: you don’t need to be an IT expert to protect yourself. The goal is not to distrust every email blindly, but to develop a reliable system for spotting scams – without unnecessary panic.
In this article, you’ll learn:
✅ How to identify typical scam emails at a glance
✅ The modern tricks scammers are using right now
✅ Simple tools to help you stay safe
✅ What to do if you accidentally click on a link
So, take a deep breath, grab a coffee, and let’s get started – your digital self-defense begins now.
1. The 5-Second Check: Spot the First Warning Signs
Before you click a link, open an attachment, or reply to an email, pause and perform a quick but effective check.
Small details often reveal whether the message is legitimate or a scam attempt.
Work through these points systematically:
1. Do you know the sender?
-
Expected email? If you weren’t expecting communication from the company, be cautious.
-
Check the sender address: Click on the displayed name to see the full email address. Scammers often use similar-looking domains (e.g.,
service@amaz0n.deinstead of@amazon.de). -
Unknown sender? If you don’t recognize the contact: better ignore it or verify it separately (not via the email!).
2. How is the greeting?
-
Generic greetings like “Dear Customer”, “Hello User”, or “Dear Account Holder” are strong phishing indicators. Legitimate companies usually use your first or last name.
-
No greeting at all? That’s also suspicious – professional communication rarely omits a personal salutation.
3. Is urgency being pushed?
Phishing emails often use psychological pressure to rush you. Common red flags include:
-
Threats: “Your account will be suspended!”, “Final notice before legal action!”
-
False urgency: “Act now or lose your data!”, “Today only: confirm your account details!”
-
Tempting offers: “You’ve won! Click now to claim your prize.”
4. Are there language errors?
-
Spelling and grammar mistakes: Professional companies don’t send out messages with obvious errors. Many scams are auto-translated, resulting in awkward wording.
-
Odd phrasing: Foreign expressions or unnatural sentence structures (e.g., “We urgently require your response for security verification”) can indicate a scam.
5. Are there suspicious links or attachments?
-
Hover over links (without clicking!) to see the real URL. If it doesn’t match the sender – hands off!
-
Unsolicited attachments (e.g., invoices, “security checks” as PDFs or ZIP files) are often malicious.
Just a few seconds of checking can protect you from a scam.
If even one point seems suspicious: ignore the email or contact the company directly via its official website.
2. System over Stress: The 4-Step Analysis
Phishing emails are becoming more sophisticated – but with a structured check, you can spot even professional-looking scams.
Work step-by-step instead of letting alarming messages throw you off.
Step 1: Check the sender – the crucial first glance
The email address is the most reliable clue. Here’s how:
-
Check the domain: Legit companies use their own domains, not free email services.
-
Real:
service@paypal.com -
Fake:
paypal.kundencenter@gmail.comorsupport@paypal-security.org
-
-
Look out for:
-
Typos (
paypai.cominstead ofpaypal.com) -
Subdomains (
paypal.service.secure.com– onlysecure.comis the real domain) -
Odd endings (
.biz,.xyz,.online)
⚠️ Even a “real-looking” address can be spoofed. When in doubt, never reply directly – instead, find the contact via the official website.
-
Step 2: Check the link target – the hover method
Every button or link could lead to a scam site. Safely check like this:
-
Hover your mouse over the link (without clicking!).
-
Check the URL shown in your browser or email client.
-
Safe:
https://www.amazon.de/mein-konto -
Dangerous:
-
https://amzn-login.security.xyz(wrong domain) -
http://amazon.de.secure-update.com(tricky subdomain) -
Short links (e.g.,
bit.ly/...) – could hide anything.
💡 If unsure, type the web address manually or use a bookmark.
-
-
Step 3: Analyze language and tone – the psychology of scammers
Phishing emails play on emotions. Common patterns:
-
Threats & urgency:
-
“Your account will be locked in 24 hours!”
-
“Final warning: unauthorized login detected!”
-
“Billing verification required – act now!”
-
-
Enticing rewards:
-
“You’ve won €500 – claim now!”
-
“Exclusive offer: free gift card!”
-
-
Typical signs:
-
Generic greeting (“Dear User”)
-
Bad translations (“Your access was compromised”)
-
Unnaturally formal or awkward language
💡 Counter-strategy: Legit companies write in a factual tone and include specific details (e.g., invoice numbers).
-
Step 4: Attachments? Big red flag!
Attachments are a common malware vector – especially:
-
Dangerous file types:
-
.exe,.scr,.js(executable programs) -
.zip,.rar(compressed malware) -
.docm,.xlsm(macro viruses in Office files)
Rule: Never open unexpected attachments – even supposed “invoices” or “contracts”.
💡 Ask the sender via a separate channel if the file is legitimate. Use tools like VirusTotal.com to check suspicious files.
-
Safe actions checklist:
-
Verify sender’s domain (no free-mail addresses!)
-
Hover-check all links
-
Language check: threats/rewards? → Be suspicious!
-
Delete doubtful attachments – never open them!
With this system, you break the urgency scammers try to create.
3. What to Do in an Emergency
If you’ve clicked by mistake – stay calm and act methodically.
No one is immune – it only takes one distracted moment. The key: no panic! A clear head and structured steps can limit or prevent damage.
Your personal action plan:
1️⃣ Disconnect the device from the internet immediately
-
Why? Many malicious programs try to instantly transmit data or download more malware.
-
How? Turn off Wi-Fi or mobile data, enable flight mode, or unplug the network cable.
2️⃣ Run a full virus scan
-
Use your antivirus (e.g., Windows Defender, Avast, Bitdefender) in safe mode with networking disabled.
-
If you don’t have one installed, use free tools like:
-
Malwarebytes Free
-
ESET Online Scanner
-
3️⃣ Change your passwords immediately
-
Especially if you entered personal credentials or use the affected device for:
-
Online banking
-
Email
-
Online shops
-
Social media
-
-
Start with key accounts (email, bank, PayPal, Amazon, social media) – each with a strong, unique password. Use a password manager like Bitwarden or KeePass if needed.
4️⃣ Inform your bank or payment provider
-
If account data may be compromised:
-
Block your card via 📞 116 116 (free, 24/7 in Germany)
-
Notify your bank or provider (e.g., PayPal)
-
Change your credentials there as well
-
-
Many banking apps allow instant blocking – use it!
5️⃣ Report it to the police
-
Cybercrime is not a minor offense – even attempts matter.
-
File a report:
-
Online via polizei.de → select your state → “Internet crime”
-
In person at your local police station
-
-
Have ready:
-
The full email
-
Sender address and links
-
Time/date of the click
-
Screenshots, if available
-
✅ Bonus tip: Check other devices if they sync files or logins (laptop, tablet, phone).
Conclusion: How to Spot Fake Emails in 2025
Fake emails are sadly part of everyday life in 2025 – but with the right knowledge, you don’t have to fall victim. Watch for common red flags like generic greetings, suspicious sender addresses, or sudden urgency.
With a structured 5-second check, a deeper look at links, language, and attachments, plus the right emergency response, you can protect yourself effectively – without needing tech expertise.
Remember: the calmer and more systematic you are when handling a suspicious email, the better you can uncover scams.
And if something does go wrong, the most important things are: stay calm, act fast, and get help.
Digital security starts with awareness – and knowing what to look for.