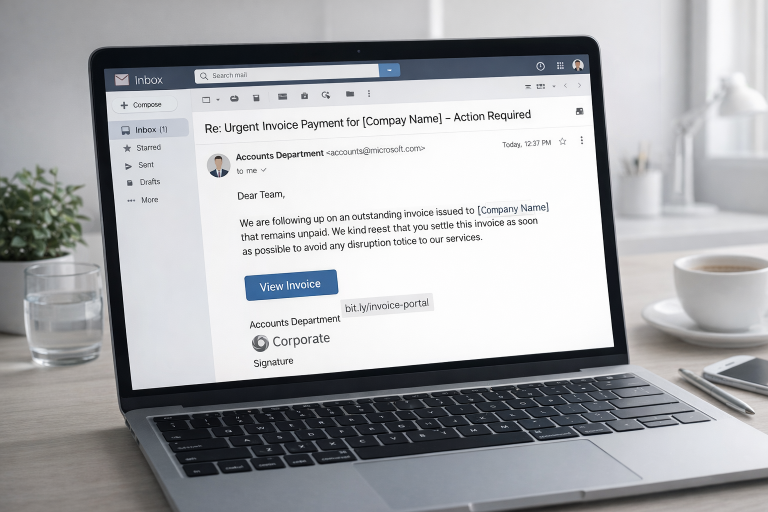
Imagine this: It’s an ordinary Monday morning. The coffee machine is running, your team is logging in – and then, silence. Every computer screen shows the same chilling message:
“All your files have been encrypted. Pay within 72 hours or lose everything.”
In an instant, the entire business grinds to a halt. Customer records are inaccessible, invoices can’t be issued, emails are frozen – operations are paralyzed. The attackers leave no doubt: only a ransom payment will restore access.
Ransomware has become one of the biggest threats to modern companies. Criminals play a ruthless game: they don’t just encrypt files, they often threaten to leak sensitive data publicly if payment isn’t made. And it’s not only large corporations in the crosshairs – small and medium-sized businesses, law firms, healthcare providers, and even freelancers are increasingly targeted.
While the situation feels overwhelming in the moment, there is a way forward. What matters most is staying calm, acting quickly, and following a clear, structured plan.
This guide will walk you through exactly what to do when ransomware strikes – from the immediate first steps, to communication strategy, to building long-term resilience so your organization comes back stronger.
Step 1: Stay calm and disconnect
Your first reaction may be panic. You might feel the urge to click on the ransom message, restart the computer, or even try to “fix it” yourself. Resist that instinct. Every second matters now – and what you do in the first minutes can determine the overall impact.
The priority is simple: stop the spread. Ransomware is designed to move fast, often jumping from one machine to another across shared drives, networks, or even email. Think of it like a fire breaking out in your office: the faster you isolate it, the less damage it can cause.
Here’s what you should do immediately:
-
Disconnect from the network: Unplug the Ethernet cable or disable Wi-Fi on the infected device. This prevents the ransomware from reaching other computers or servers.
-
Remove external media: If you have USB drives, external hard disks, or even smartphones connected, unplug them at once. Otherwise, the malware can encrypt these devices too.
-
Isolate, don’t power off: Unless instructed by your IT team, don’t turn off the machine. Shutting it down can sometimes corrupt evidence that forensics teams need later. Simply disconnect it from all networks and leave it powered on until experts take over.
-
Contain at scale: If multiple devices are showing signs of infection, consider temporarily disconnecting entire parts of the network (e.g., Wi-Fi routers, switches) to stop further lateral movement.
Remember: containment is your first line of defense. Just like in a fire drill, your actions should be swift, precise, and calm. Once the ransomware is cut off from spreading, the damage is limited to already infected systems – buying your IT team crucial time to respond.
Step 2: Inform and escalate
Once the immediate threat is contained, the next critical move is communication. A ransomware attack is not just an IT problem – it’s a business-wide emergency that requires leadership, coordination, and in many cases, external support.
Here’s how to proceed:
-
Notify your IT/security team immediately
Don’t try to handle this in silence. Inform your internal IT department or your managed service provider as soon as possible. They need to assess the scope, secure systems, and begin forensic analysis. -
Escalate to management and decision-makers
Leadership must be aware right away. They will be the ones to make strategic calls on crisis communication, potential downtime, insurance notifications, and legal implications. -
Follow your incident response plan (IRP)
If your organization has an IRP in place, this is the time to activate it. Roles and responsibilities should already be defined – from technical actions to executive decision-making. -
Report to authorities and regulators
Depending on your region and industry, there may be a legal obligation to report ransomware incidents – especially if personal data is compromised (e.g., GDPR in the EU, HIPAA in the US healthcare sector). Law enforcement agencies and national CERTs (Computer Emergency Response Teams) can often provide guidance and may already be tracking the ransomware variant. -
Communicate internally with staff
Employees need clear instructions – for example, not to reconnect their devices, not to open suspicious emails, and to report any unusual behavior on their machines. Silence breeds confusion; structured updates create control.
Key principle: A ransomware attack is as much about managing the people as it is about managing the technology. Quick, transparent escalation ensures the right decisions are made and prevents the situation from spiraling further out of control.
Step 3: Assess the damage
With the threat contained and the right people informed, the next priority is to understand the scope of the attack. You can’t plan recovery until you know exactly what’s been hit. This stage is all about visibility and documentation.
Here’s what to focus on:
-
Identify affected systems
-
Which devices show signs of encryption or ransom notes?
-
Are servers, cloud accounts, or shared drives compromised?
-
Is the infection limited to a few endpoints, or is it organization-wide?
-
-
Check the integrity of backups
Backups are your lifeline – but ransomware often targets them, too.-
Are backups still accessible and unencrypted?
-
Do you have an offline or offsite copy (e.g., on tape, cold storage, or a secure cloud)?
-
When was the last clean backup made?
-
- Document everything
-
-
Take screenshots of ransom notes and filenames.
-
Record timestamps of when issues first appeared.
-
Keep logs from firewalls, servers, and antivirus solutions.
This evidence is crucial for forensic teams, insurance claims, and regulatory reporting.
-
-
-
Look for signs of double extortion Many ransomware groups not only encrypt data but also exfiltrate it before locking systems. Indicators of unauthorized data transfer should be taken seriously – this raises compliance and privacy concerns.
-
Avoid assumptions Just because one device looks unaffected doesn’t mean it’s clean. Attackers often establish persistence or backdoors. Treat all systems as potentially compromised until verified by professionals.
Key takeaway: The goal of Step 3 is clarity, not recovery. You’re building a factual picture of the incident so your response team can prioritize what to restore, what to rebuild, and where the risks are greatest. Acting without this assessment often leads to reinfection or overlooked vulnerabilities.
Step 4: Do NOT pay the ransom
When faced with locked systems and mounting pressure, paying the ransom can feel like the only option. The attackers promise quick recovery, and every minute of downtime costs money. But here’s the hard truth: paying rarely solves the problem – and often makes it worse.
Here’s why payment is strongly discouraged:
-
No guarantees
Cybercriminals may not deliver the decryption key after payment, or they may provide a faulty one that only partially restores data. Many victims who paid found themselves empty-handed. -
Repeat targeting
Once you pay, you’ve marked your organization as a profitable target. Attackers share information on paying victims, increasing the risk of future attacks. -
Legal and ethical concerns
In some regions, ransom payments may be illegal if they fund sanctioned groups or terrorist organizations. Even when legal, paying supports the criminal ecosystem, encouraging further attacks on others. -
Hidden costs
Even if decryption works, recovery isn’t instant. Systems still need to be cleaned, vulnerabilities patched, and security improved. Paying doesn’t save you from downtime, reputation loss, or regulatory scrutiny.
Instead of funding criminals, invest resources where they matter:
-
Professional recovery from clean backups.
-
Forensic investigation to identify how attackers gained access.
-
Stronger defenses to prevent a repeat incident.
Key principle: Paying ransom is a gamble with no real upside. Focus on recovery and resilience – the money you might spend on criminals is far better invested in securing your future.
Step 5: Contain, clean, restore
Once the immediate crisis has been stabilized and a damage assessment completed, it’s time to move into recovery. This is where your IT experts or external response team take the lead. The process is rarely quick, but following the right order ensures that recovery is safe, thorough, and sustainable.
Here’s how it typically unfolds:
-
Contain the attack
-
Segregate compromised systems from the rest of the network.
-
Block malicious IPs, domains, and user accounts that attackers may have leveraged.
-
Disable remote access points if there’s evidence of exploitation.
Goal: prevent any remaining ransomware processes from spreading further or reinfecting newly restored systems.
-
-
Clean infected systems
-
Affected machines should not simply be “unlocked” – they must be wiped and rebuilt.
-
Reformat drives, reinstall operating systems, and apply the latest security patches.
-
Scan for persistence mechanisms such as scheduled tasks, registry changes, or backdoors.
In other words: treat every infected endpoint as untrustworthy until fully rebuilt.
-
-
Restore from backups
-
Use only verified, clean backups – tested for integrity and free from malware.
-
If possible, restore to new hardware or virtual environments rather than directly onto old machines.
-
Prioritize critical business functions first (email, ERP, finance) to resume operations quickly.
-
Test before going live again
-
Verify system functionality and confirm data integrity before reconnecting to the network.
-
Conduct staged rollouts, starting with a small group of systems to ensure no reinfection occurs.
-
Monitor closely for anomalies during the first hours and days of restored operation.
Reality check: This process may take several days – sometimes weeks, depending on the scale of the incident. Rushing can backfire, leading to reinfection and more downtime. A methodical, step-by-step recovery is the safest path to long-term stability.
Step 6: What this attack should change
Every ransomware attack is a brutal but valuable teacher. Once systems are restored and operations are back on track, the work isn’t finished. In fact, the most important phase begins here: learning from the incident to prevent it from happening again.
Conduct a thorough post-incident review with all relevant stakeholders – IT, management, compliance, and even end users where applicable. Key questions to address include:
-
How did the attacker gain entry?
Was it a phishing email, stolen credentials, weak passwords, an unpatched vulnerability, or misconfigured remote access? -
What worked in your defense?
Did firewalls, detection tools, or employee reporting slow the spread? Recognize strengths so they can be reinforced. -
What failed or needs improvement?
Was detection too slow, communication unclear, or backups outdated? Failures should be documented transparently, not hidden. -
How do we strengthen resilience moving forward?
The ultimate goal is to come out of the crisis more secure than before.
Key measures for long-term resilience:
-
Regular offline backups & restoration drills
Backups must be stored offline (or immutable in the cloud) and tested regularly to ensure they can be restored under pressure. -
Security awareness training
Employees remain the first line of defense. Teaching them to recognize phishing, social engineering, and unsafe practices effectively turns them into a human firewall. -
Adopt Zero Trust principles
Never assume trust based on location or credentials alone. Verify every access attempt, minimize privileges, and segment networks. -
Harden your technology stack
Implement strong endpoint protection, enable multi-factor authentication (MFA) across all accounts, and invest in continuous monitoring and threat detection tools. -
Simulate and test
Run regular tabletop exercises and ransomware simulations. This ensures both staff and systems are prepared for real-world pressure.
Key principle: A ransomware incident doesn’t have to define your organization – but how you respond and improve afterward absolutely will. The strongest companies are those that treat an attack not only as a crisis but also as a catalyst for building a culture of resilience.
This article looks at what really goes wrong in the first six hours after a cyberattack. Not in theory, but in reality. Because cybersecurity rarely fails because of missing tools. It fails when pressure, confusion, and human reactions take over.

Conclusion: What to do in a ransomware attack step by step
A ransomware attack is one of the most disruptive incidents an organization can face. Systems are locked, data becomes inaccessible, and decisions must be made under pressure. In these moments, panic only increases the damage. A structured response, however, creates clarity and control.
Effective ransomware response follows a clear sequence: isolating affected systems to stop the spread, escalating the incident so responsibility is clear, assessing the scope of the damage, and focusing on safe recovery instead of paying a ransom. Containment, cleanup, and restoration from trusted backups stabilize operations, while post-incident learning strengthens defenses and reduces future risk.
The key lesson is simple: ransomware response is not only about recovering systems, but about being prepared. Organizations with a clear response plan in place can limit damage, shorten downtime, and turn a crisis into a step toward long-term resilience.
I recommend to read to follows articels
AI-Phishing Emails: Why They’re Harder to Detect Than Ever
Cybersecurity 2025: The Biggest Risks for Businesses – and How to Protect Your Company
Why Virus Protection Alone Is Rarely Enough – and Why Knowledge Is the Key
Incident Response Guide
When a cyber incident hits, small businesses often lose valuable time trying to figure out what comes next.
This guide is designed for decision makers who need clarity, not complexity. It walks you through the critical first steps, highlights common mistakes to avoid, and helps you stay focused when pressure is high.
Instead of reacting blindly, you’ll know how to respond calmly, protect your business, and make informed next decisions.
Download the Incident Response Guide and prepare before the incident happens.D