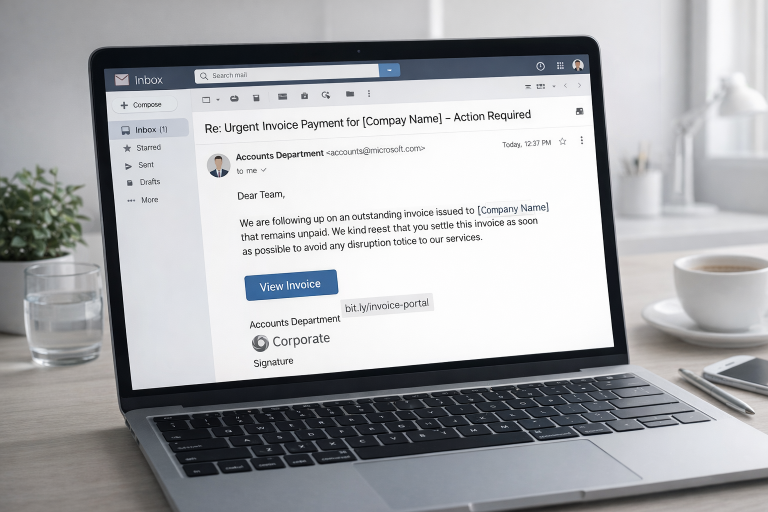
Phishing, Trojans, and fake emails—you’ve probably heard these terms before. However, many people underestimate the actual danger. Cybercriminals are becoming increasingly sophisticated and are able to mimic authentic messages from banks, parcel services, or online shops. Their goal: your personal data, your online banking, or even your entire system.
The insidious thing about it is that often a single careless click is enough to give the attackers access. The consequences range from emptied accounts to identity theft – a nightmare that causes enormous stress and annoyance.
The good news is that with a little attention and knowledge of the most important warning signs, you can protect yourself effectively. In this article, you will learn how to recognize phishing attempts and Trojans in time, what typical characteristics appear again and again, and what simple steps you can take immediately.
In short: after reading this article, you will be able to confidently classify suspicious emails or files and make the right decision when in doubt.
1. Check the sender address
Phishing emails often look deceptively authentic at first glance: the logo, colors, even the signature appear professional. But the crucial clue is often hidden in the sender’s address.
While reputable companies use clear and traceable addresses – such as support@paypal.com or service@deutsche-bank.de – fraudsters resort to tricks:
-
They use similar-looking domains, such as support@paypall-security.net (with a double “l”) or kundenservice@deutsche-b4nk.com .
-
They replace letters with similar-looking characters. A lowercase “l” can quickly look like an “i,” and the “o” is replaced by a zero.
-
Sometimes they even use freely available email addresses from services like Gmail or Outlook: paypal-customerservice@gmail.com – which, of course, would never be official.
👉 Practical tip:
-
Click on the sender’s name in your email program and view the full address. Often, only then can you tell if something is wrong.
-
If you’re unsure, enter the domain (e.g., “paypall-security.net”) into a search engine. You’ll usually find immediate indications that it’s a scam site.
-
Never trust the displayed name alone, such as “PayPal Support” or “Sparkasse Customer Service.” These can be faked in seconds.
This initial check is extremely important because it’s often the only detail that reveals a fake email. Getting into the habit of quickly checking the address of every email drastically reduces your risk.
2. Grammatical and spelling errors
A very common warning sign for phishing emails and fake messages is linguistic inconsistency. Official companies invest in professional communication – their emails are usually correctly worded, well-structured, and free of major errors. Cybercriminals, on the other hand, often rely on automated translations or simply have no interest in linguistic accuracy.
Typical abnormalities:
-
Unusual wording : “Please confirm your data” or “Your account will be blocked” – such sentence structures sound unnatural.
-
Incorrect salutation : Instead of a personal greeting like “Dear Ms. Müller,” you often only read a general “Dear Customer” or “Hello User.”
-
Spelling mistakes : Words are misspelled or contain unnecessary spaces (“PayPal”, “On lineBanking”).
-
Unprofessional style : Some emails are noticeably short or seem overly friendly, e.g., “Dear friend, please help me quickly!” – which is not appropriate for a bank or insurance company.
👉 How to expose such emails faster:
-
Read suspicious messages deliberately slowly. Mistakes often only become apparent upon closer inspection.
-
Ask yourself: Would my bank or online shop really write like this? Reputable companies value their public image and would never send emails full of errors.
-
Do the “language test”: If the email sounds like it came from a bad translation program, you can be almost certain that something is wrong.
There are exceptions, however: Some phishing emails are now almost linguistically perfect. Therefore, you should never use spelling and grammar as the sole criteria—but they are a valuable clue that should immediately make you suspicious.
3. Urgency & scaremongering
One of cybercriminals’ most effective tools is fear. Many phishing emails use time pressure or threaten consequences to force you to react quickly and rashly. This psychological tactic works frighteningly well—because under stress, we often act impulsively.
Typical examples:
-
“Your account will be closed in 24 hours if you do not respond!”
-
“Final warning: We have detected suspicious activity. Take immediate action!”
-
“Today only: Confirm your details to continue using the service.”
Such wording is deliberately designed to make you fear losing something important – be it access to your bank account, your Amazon orders, or even your own identity.
👉 How to distinguish real news from fake news:
-
Reputable companies rarely set deadlines of just a few hours. If there’s a real problem, you’ll usually receive multiple notifications via various channels (e.g., by mail, app notification, or phone).
-
Drastic consequences (“immediately deleted account”) are almost always fake. Banks or payment services give you time to resolve your concerns.
-
Emotionally charged language (“Last chance!”, “Act immediately!”) has no place in professional business communication.
👉 Practical tips:
-
Take a deep breath and never click on links or buttons in the heat of the moment.
-
If you’re unsure, open your provider’s website manually in your browser (e.g., www.paypal.com ). There you’ll immediately see whether there really is a warning or message.
-
If in doubt, call customer service directly. This way, you’ll avoid the trap.
Remember: Urgency is one of the strongest warning signs. Those who pressure you usually want one thing: to stop thinking and blindly click on the link.
4. Suspicious links
Phishing emails almost always contain links or buttons that lead to fake websites. These pages are often designed to look deceptively real and imitate well-known companies like PayPal, Amazon, or your bank. They then ask you to enter sensitive information—such as your login details or credit card number.
The trick: The text of the link looks harmless, but behind it lies a completely different address.
Typical examples:
-
The email text says: www.paypal.com , but if you hover over it with your mouse, you will see: http://pay-pal.verify-account.cn
-
A button is labeled “Log in now” but redirects you to a completely unknown domain such as login.secure-portal.info .
-
Some links look legitimate at first glance, but contain tiny variations, e.g., www.sparkassse.de (with three “s”).
How to identify suspicious links:
-
Use the hover effect: Hover your mouse over the link (without clicking!). You’ll see the actual destination address at the bottom of your browser.
-
Pay attention to HTTPS: Reputable sites always begin with https:// . If the “s” is missing, you should immediately be suspicious.
-
Check your domain carefully: The part directly before the ending (.de, .com, .net) is crucial. A page like amazon.kundenservice.support.de doesn’t belong to Amazon, but to “support.de.”
-
Avoid cryptic characters: Long URLs full of numbers, special characters, or strange additions are often suspicious.
Practical tips:
-
Always enter important addresses manually in your browser instead of following links in emails.
-
Use browser plugins or security software that automatically block dangerous websites.
-
If you’re unsure, copy the URL (don’t click it!) and search for it. You’ll often find warnings from other users right away.
👉 Remember: Links are the number one entry point for phishing. Always check them twice before clicking.
5. File attachments with caution
A particularly popular way for attackers to spread malware such as Trojans or ransomware is through file attachments in emails. Even a careless double-click can cause malware to install itself unnoticed on your computer – often with serious consequences.
Typical traps:
-
ZIP archives : Often contain alleged invoices or delivery notes that actually hide an executable file (.exe).
-
Office documents (Word, Excel, PowerPoint) : Files with enabled macros are dangerous . Attackers disguise malicious code as a “document” that supposedly contains a confirmation or reminder.
-
PDF files : Usually more secure, but can also be compromised and redirect to malicious links.
-
Attachments with double extensions : e.g., “Invoice.pdf.exe.” At first glance, they look like a PDF, but in reality, they are an executable program.
How to protect yourself:
-
Never open attachments without thinking. If you weren’t expecting a file, you should be especially cautious—no matter how genuine the email appears.
-
Check the sender critically. Even if the email appears to come from a known contact, their account may have been hacked. If in doubt, ask directly.
-
Display file extensions. Enable the option to display full file extensions in your operating system—this way you can immediately identify duplicate extensions or incorrect file types.
-
Use a virus scanner. Many modern security programs automatically scan attachments before you open them.
Practical example:
You receive an email with the subject “Final Reminder – Outstanding Invoice” from an unknown sender. The attachment contains a file called “Invoice.zip.” Your natural instinct would be to open the file – but that’s where the trap lies. In 9 out of 10 cases, it’s not a document, but malware.
👉 Remember: Only open attachments you expected and whose origin you clearly know. Everything else belongs immediately in the trash.
6. Unusual behavior on the PC
Some Trojans and malware sneak in despite all precautions. They’re often programmed to run as inconspicuously as possible in the background. But they rarely remain completely invisible. Certain signs can indicate that something suspicious has taken root on your system.
Typical warning signs:
-
Sudden slowdown : Your computer or smartphone responds unusually sluggishly, even though you don’t have any large programs open.
-
Unknown programs or processes : Applications that you don’t recognize appear in Task Manager (Windows) or Activity Monitor (Mac).
-
Strange error messages : Programs crash more frequently or windows appear that you cannot understand.
-
Unusual internet activity : Your internet connection is noticeably slow, or you notice traffic even though you are not downloading anything.
-
Changed settings : Homepage in the browser suddenly different, unknown toolbars or new apps that you never installed.
-
Antivirus software disabled : Some Trojans attempt to disable or block security programs.
What you should do if you suspect something:
-
Start system scan : Immediately run a full scan with your antivirus or antimalware software.
-
Check programs : Look at the list of installed programs and remove anything unknown or suspicious.
-
Disconnect from the network : If you think sensitive data is at risk, disconnect your device from the internet for now.
-
Perform updates : Make sure your operating system and software are up to date – many Trojans exploit known security vulnerabilities.
-
Use backup : In the worst case, the only solution is to reinstall the system and restore data from a clean backup.
Practical tip:
Perform simple checks regularly—for example, looking at startup programs or the list of active processes. This will help you notice changes more quickly.
👉 Remember: If your computer suddenly behaves differently, there’s usually more to it than just coincidence.
7. Use official channels
If you’re unsure whether an email, text message, or message is genuine, there’s a simple but very effective step: Contact the official source directly. Scammers want you to respond via their fake links or phone numbers—this is exactly what you should avoid.
Here’s how to do it correctly:
-
Only access websites manually : Type your provider’s address into your browser’s address bar (e.g., www.paypal.com or www.sparkasse.de ). Never follow links in emails.
-
Use the official app : Many banks and payment services offer secure apps that allow you to see immediately whether there is actually a message or warning.
-
Call directly : Only use the phone number from the official website, bank card or contract documents – never the number from a suspicious email.
-
Check your customer account : Log in directly to your account. If there is indeed a problem, you’ll find a message there.
Example:
You receive an email, supposedly from your bank, with the message: “Please click here to unlock your account.” Instead of using the link, you go directly to your bank’s official website or call the familiar hotline. In 99% of cases, it turns out there was never a problem—the email was a phishing attempt.
Extra tip:
Many companies have their own phishing reporting centers . You can simply forward suspicious emails (e.g., to spoof@paypal.com ). This not only helps you but also other customers.
👉 Remember: Never rely on information from a suspicious message – always seek information through official channels .
Conclusion: How to recognize phishing emails and Trojans – the most important warning signs
Most phishing and Trojan attacks rely on a single factor: inattention . Scammers rely on you clicking quickly in everyday life without looking closely. That’s precisely why it’s worth taking a few extra seconds to look at any suspicious message.
Check sender addresses, pay attention to spelling, don’t let yourself be pressured, and don’t open unexpected attachments. Links also deserve special attention—a quick glance at the actual destination address can save you from serious damage.
Equally important: Be sensitive to your computer’s behavior. If something suddenly stops working as usual, it’s often a warning sign that malware may have crept in. And when in doubt, it’s better to check directly with the official provider than to fall victim to a scam.
In the end, your best defense is common sense . If a message or file seems “weird,” in most cases it is. Trust your gut, stay vigilant—and make life as difficult as possible for cybercriminals.